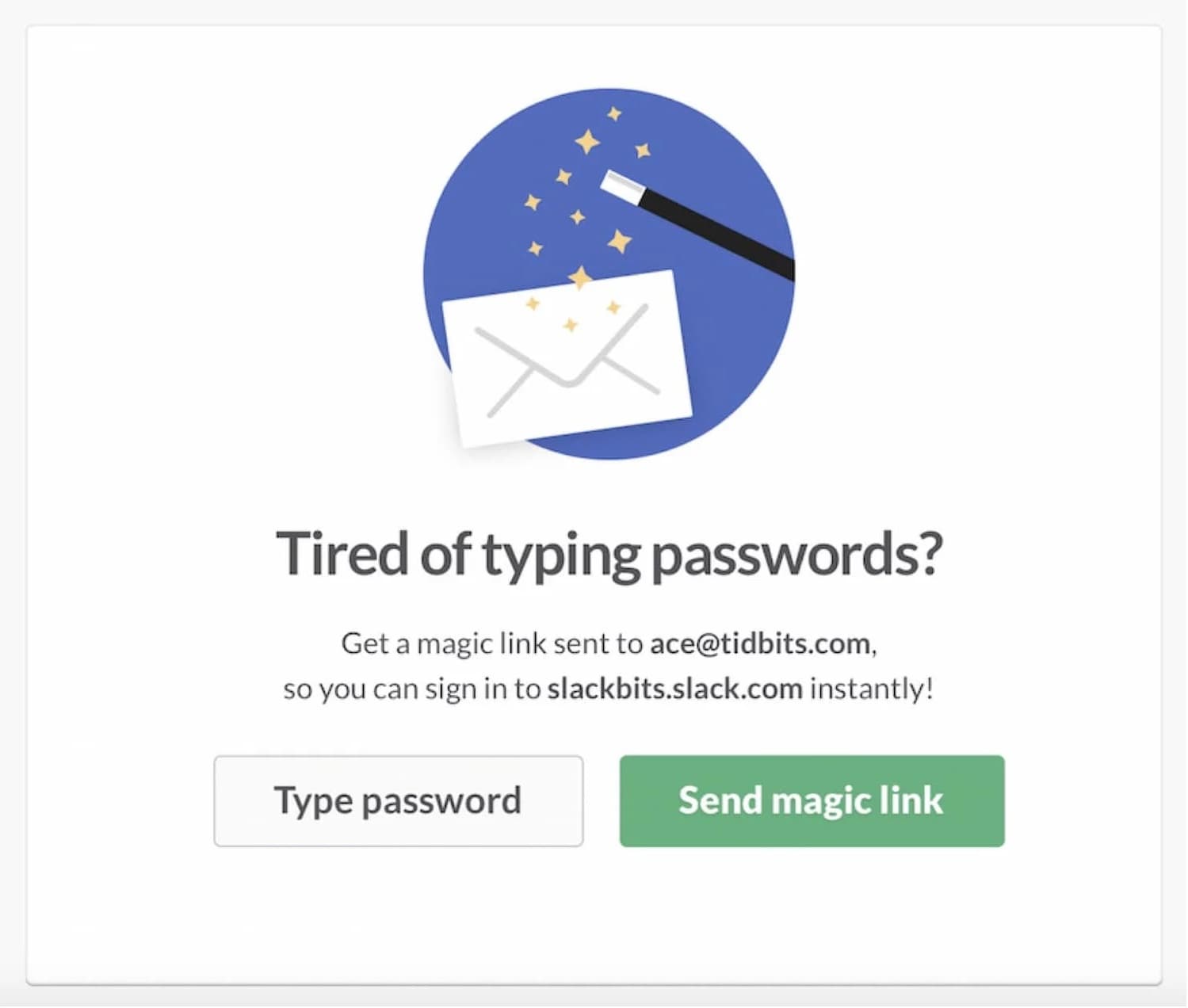
Authentication is a difficult topic. There are such a lot of phrases floating round us, from 2FA to MFA to OTP — and it could be troublesome to make sense of what we’d like and after we want it. However authentication is in all places, and generally it’s extraordinarily irritating, and generally it’s seamless. Let’s discover just a few patterns to create expertise which can be a bit extra seamless than irritating.
Now, no one wakes up within the morning hoping to lastly establish crosswalks and fireplace hydrants that day. But day-after-day, we immediate customers by means of hoops and loops to enroll and log in, to set a posh sufficient password or recuperate one, to discover a method to restore entry to locked accounts and logged-out periods.
In fact safety issues, but too typically, it will get in the way in which of usability. As Jared Spool mentioned as soon as, “If a product isn’t usable, it’s additionally not safe.” That’s when individuals begin utilizing non-public electronic mail accounts and put passwords on stick-it-notes as a result of they overlook them. As typical, Jared hits the nail on the pinnacle right here. So what can we do to enhance the authentication UX?
This text is a part of our ongoing collection on design patterns. It’s additionally part of the upcoming 4-weeks stay UX coaching 🍣 and might be in our just lately launched video course quickly.
1. Don’t Disable Copy-Paste For Passwords
It seems solely cheap to dam copy-paste for password enter to keep away from brute-force assaults. But after we accomplish that, we additionally block customers who copy-paste passwords from password managers and textual content paperwork. Because of this, they should repeatedly retype complicated, prolonged, cryptic strings of textual content — and it’s hardly ever an thrilling journey to embark on.
In truth, that’s gradual, annoying and irritating. In her speak on Authentication UX Anti-Patterns, Kelly Robinson explains that this can be a widespread anti-pattern, typically inflicting far more frustration than treatment, and therefore finest to be averted.
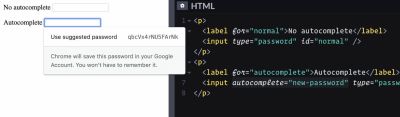
Additionally, double verify that your password fields embrace the attribute autocomplete="new-password", so browsers can immediate a sturdy auto-generated password. And the most effective bit: customers with out password managers don’t have to return with a password of their very own — as a result of often that’s a recipe for catastrophe.
2. Don’t Depend on Passwords Alone
Passwords are problematic. For instance, solely 34% of customers within the US use a password supervisor, and everyone else depends on their good ol’ reminiscence, sticky notes, and textual content information on the desktop.
Good passwords are laborious to recollect. Because of this, customers typically select easy-to-guess passwords as an alternative, together with names of their pets and family members, their birthdates, and their wedding ceremony dates. That’s removed from safe, in fact.
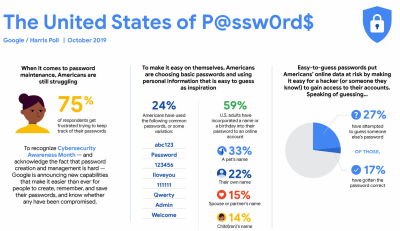
Nonetheless, we frequently overlook our passwords, generally recovering passwords 4-5 instances per week. So no marvel many people nonetheless reuse the identical password throughout a number of accounts, typically favoring comfort over knowledge security. In truth, permitting customers to decide on their very own passwords is a recipe for bother. To repair that, what if we nudge customers away from passwords?
Any sort of 2-Issue Authentication is best than passwords, and ideally, we might use a cookie that customers can opt-in for to keep away from frequent log-ins. Information-sensitive websites may need to log off customers robotically after each go to (e..g on-line banking), however less complicated websites could be higher off avoiding aggressive log-outs and permitting customers to remain logged in for 30 days and even longer.
3. Drop Strict Password Necessities
Since customers are superb at twisting and bending password guidelines (simply to overlook them shortly after the duty is finished), what if we alter our technique altogether? What if we do help prolonged and sophisticated passwords with all of the particular characters distinctive delimeters however hold guidelines comparatively pleasant?
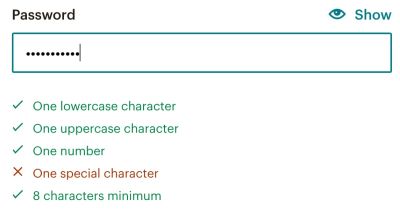
This certainly would come at the price of safety, in fact. So to guard person’s knowledge on their behalf, we use new-password to immediate safe passwords to be generated throughout sign-up, and nudge customers aggressively in direction of a 2FA setup, e.g., offering 30% off for the primary month for turning 2FA on.
The one factor required could be to attach the account with a cell phone or Google Authenticator, sort in a verification code, or confirm with a Contact-ID, and that will be it. Thus, we keep away from countless and costly password resets, which frequently trigger abandonment and frustration.
4. Social Signal-In Isn’t For Everybody
The extra delicate the information saved, the extra consideration customers count on from the interface to safety. Usability periods trace that log-in hurdles appear to be accepted so long as they’re thought-about to be “cheap”. However what’s cheap to us, as designers, isn’t essentially what’s cheap to our clients.
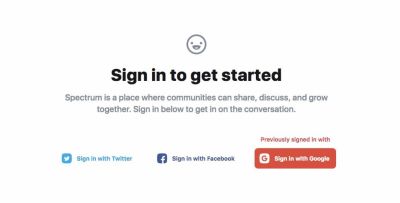
Social sign-in is an efficient instance of that. Some customers adore it as a result of it’s so quick, but others are typically against it as a result of privateness considerations. Plus, we have to adjust to GDPR, CCPA, and related laws when utilizing them.
Additionally, do not forget that some customers overlook what they signed up with final time, so it’s a good suggestion to point their earlier alternative based mostly on their earlier log-in (as illustrated above). Basically, social sign-in is a superb possibility for individuals who simply need to get issues performed, however it may possibly’t be the one possibility that we offer.
5. Exchange Safety Questions With 2FA
In an excellent world, safety questions — like those we’re being requested by a financial institution on the telephone to confirm our identification — ought to assist us forestall fraud. Basically, it’s a second layer of safety, but it surely performs remarkably poorly each by way of usability and safety. Questions on favourite pets, maiden names, and the primary faculty can simply be found by scrolling a Fb stream lengthy sufficient.
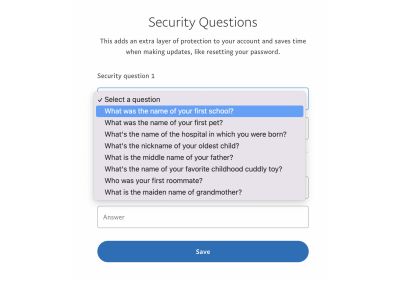
Figuring out that, customers generally reply to those questions with the exact same reply (e.g., their birthday or a location of start) and generally even use the identical password that they’ve entered initially. This isn’t actually serving to anyone. Magic hyperlinks and push notifications are far more safe, and there’s no must memorize the solutions in any respect.
6. Customers Want Choices For Entry Restoration
Nothing may be extra irritating than being locked out at simply the mistaken second. As designers, we are able to pave deliberate methods out in our interfaces with a number of alternate methods to revive entry (entry restoration stacks) and keep away from these points for good.
We frequently consider password restoration to assist customers restore their entry, however maybe serious about recovering entry is a greater perspective to take a look at the difficulty. If a person can’t log in at a given second, they aren’t actually enthusiastic about defining a model new safe password, or discovering an electronic mail or particular characters that they haven’t used earlier than. They simply must log in. And we have to assist them do exactly that.
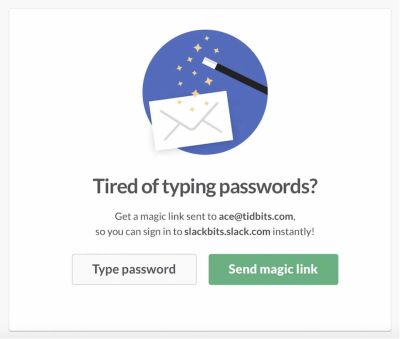
Of all of the methods for entry restoration, certainly, magic hyperlinks might be part of the entry restoration stack. Customers appear to understand simply how briskly they’ll get again in as soon as they’re locked out. Normally they work flawlessly except the e-mail doesn’t arrive, or the account is linked to an outdated electronic mail, or the e-mail inbox or telephone aren’t accessible.
Nonetheless, to make use of magic hyperlinks, customers must swap context, leaping from browser to the mail shopper after which again to the browser. It may need been sooner to immediate customers to sort in a code on their telephone to get in as an alternative. By hook or by crook, to keep away from lock-outs, we present a number of choices to ensure a speedy restoration, and a mixture of choices works finest:
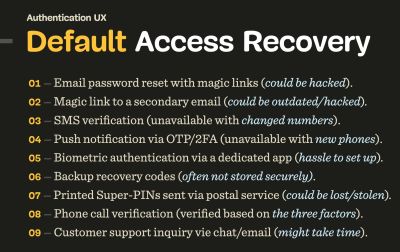
-
Ship a magic hyperlink for log-in by way of electronic mail.
Don’t require customers to retype a password, or set a brand new one. Customers won’t have entry to electronic mail, or it could possibly be hacked. -
Ship a magic hyperlink for log-in to a secondary electronic mail.
Sadly, the secondary electronic mail is usually outdated, or the person may need no entry to it. -
Ship an SMS verification URL/code to a cell phone.
This selection received’t work for customers who’ve bought a brand new telephone, or don’t have entry to their SIM-card (e.g. when travelling overseas). -
Ship a push notification by way of OTP/2FA.
This selection received’t work for customers who’ve bought a brand new telephone and haven’t arrange OTP/2FA simply but, or don’t have entry to their outdated telephone. -
Biometric authentication by way of a devoted app/Yubikey.
This selection received’t work for customers who don’t have an OTP/2FA setup but, or have bought a brand new telephone/Yubikey. -
Kind backup restoration codes.
Not each person may have backup restoration codes close by, but when they do, they need to at all times override account lock-out. Typically backup restoration codes are despatched by way of a postal service, however they could possibly be misplaced/stolen. -
Telephone name verification.
Customers could possibly be referred to as on their (new) telephone, and so they’d must reply just a few inquiries to confirm their idemtity. Ideally, it will be one thing that they know (e.g. newest transactions), one thing that they’ve (e.g. bank card) and one thing that they’re (e.g. face recognition by way of a video name). -
Buyer help inquiry.
Ideally, customers might restore entry by chatting with an agent by way of stay chat, WhatsApp/Telegram, video name or electronic mail (which is often the slowest).
It’s not a good suggestion to ship randomly generated passwords by way of electronic mail and require a brand new password setup when a person lastly manages to log in. That’s not safe, and it’s at all times a trouble. As an alternative, but once more, nudge customers in direction of a 2FA setup, to allow them to recuperate entry by accessing a code from the app put in on their telephone or SMS (which is much less safe, nonetheless.)
Wrapping Up
Authentication is at all times a hurdle. But when the interface is troublesome to take care of, customers grow to be remarkably artistic in bending the foundations to make it work and overlook the password the second they full a transaction.
Maybe we must always give our customers not less than an opportunity to get to know our web site or app earlier than creating too many boundaries for them. Ideally, we’d like a 2FA setup for everybody, however we have to get there first. And a path there’s paved with a seamless, good authentication UX — with out difficult guidelines and restrictions, and ideally the one which customers received’t even discover.
Meet “Good Interface Design Patterns”
If you’re enthusiastic about related insights round UX, check out Good Interface Design Patterns, our shiny new 8h-video course with 100s of sensible examples from real-life tasks. Loads of design patterns and tips on all the things from accordions and dropdowns to complicated tables and complicated internet varieties — with 5 new segments added yearly. Simply sayin’! Verify a free preview.

100 design patterns & real-life
examples.
8h-video course + stay UX coaching. Free preview.
Helpful Sources
Associated Articles
In the event you discover this text helpful, right here’s an outline of related articles we’ve revealed through the years — and some extra are coming your method.