Intro
Wow! It’s been some time since I’ve blogged. I’ve simply been so swamped with CIPP that I’ve simply let the running a blog go completely. It’s a disgrace as a result of I feel out of all my hobbies it’s one I get pleasure from essentially the most. It’s at all times good serving to others obtain their scripting goal. I even received a few LinkedIn questions asking if I used to be finished with running a blog however I’m not. Writing at all times provides me some extra piece of thoughts so I’ll attempt to catch up once more. I do know I’ve mentioned that earlier than however this time I’ll comply with by means of. I’m sitting down proper now and scheduling the discharge of 5 blogs in a single go. No extra whining and no extra ready.
At this time we’re beginning with a easy one that usually will get missed. One in every of my mates considerably just lately made the comply with LinkedIn publish:
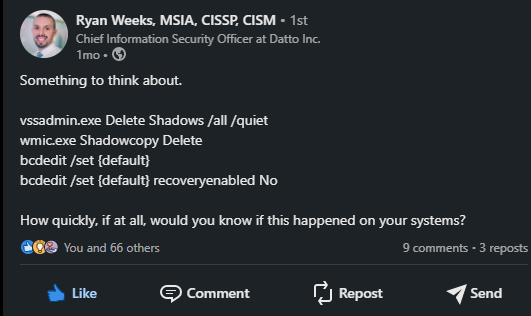
It felt sort of serendipitous that he made this publish proper earlier than my session at Dattocon. My session there was about defending your self towards these form of assaults. So, as we speak I’m sharing with you methods to monitor in case your VSS snapshots haven’t been deleted, and if they’re above the rely that you just’ve specified.
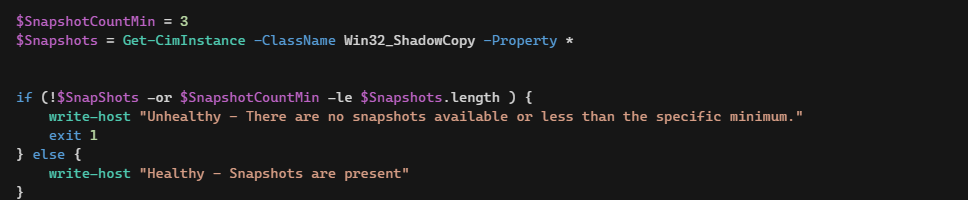
VSS Monitoring script
|
|
Now this can be a fairly brief one proper? Don’t you hate it whenever you anticipate a weblog for months and don’t get greater than a spoon full? I do. So let’s resolve one other downside in Ryan’s publish. When attackers hit they typically edit the bcd file means earlier than executing the precise assault, so it’s a superb factor to sign on;
|
|
Two pretty simple scripts, however each may prevent loads of headache.
All the time, Comfortable PowerShelling. 🙂