Do you want (once more) to regulate your password generator after a coverage change? One of the best ways to keep away from password generator changes after a coverage change, is to generate passwords relying on the present Area Password Coverage. Right here is the way it works.
Studying the password insurance policies of a website
First we wish to learn out the password insurance policies of the area. Through Server Supervisor > Instruments there are two methods to search out the insurance policies:
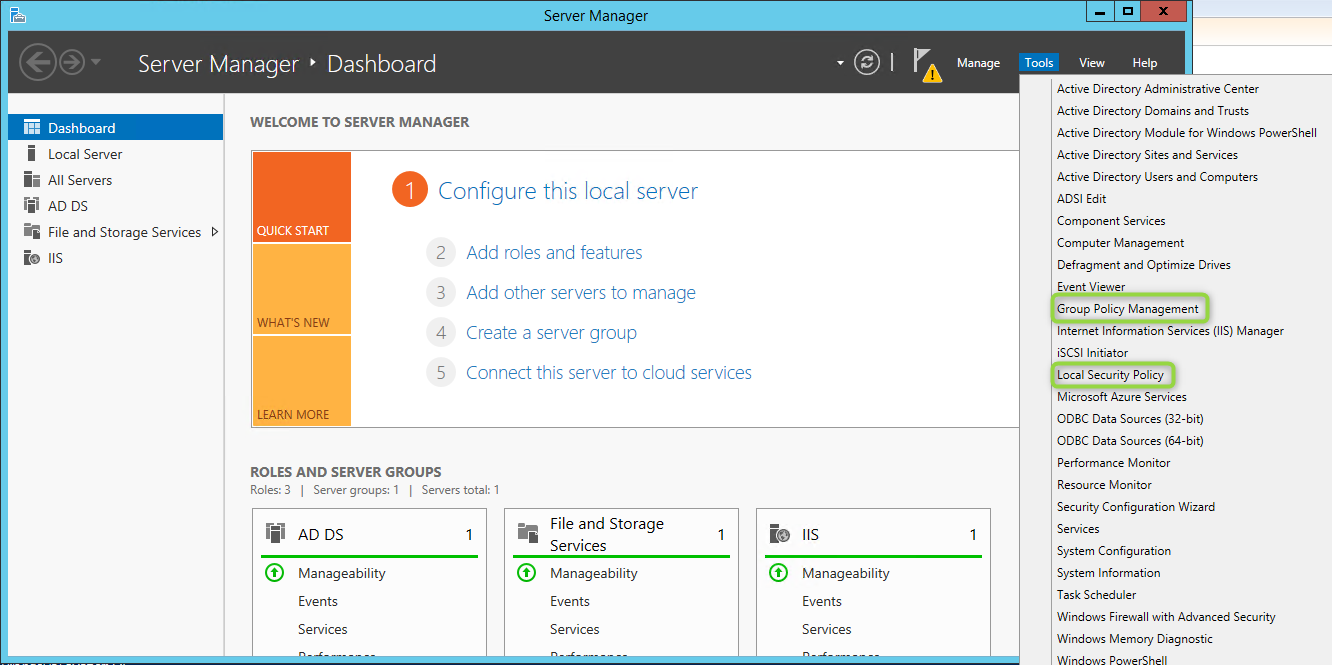
The Group Coverage Administration software reveals you all insurance policies underneath the area and default area coverage, together with the password coverage.
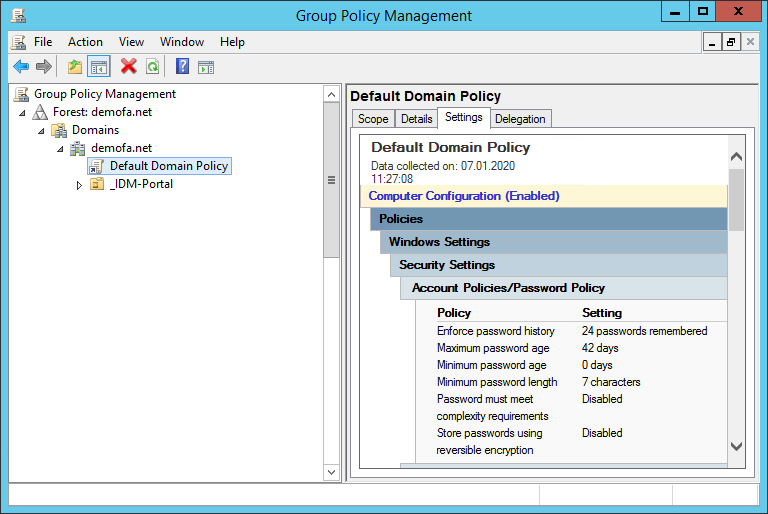
The password insurance policies will also be displayed through “Native Safety Coverage”, however will also be modified with the suitable permissions.
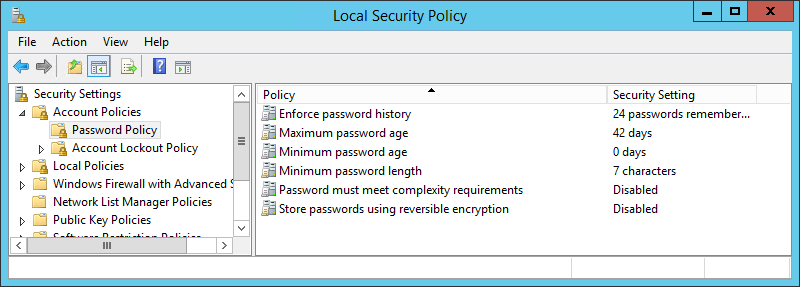
Password Coverage Properties
The Password Coverage consists of the next properties, which we will configure:
- PasswordHistoryCount
- MaxPasswordAge
- MinPasswordAge
- MinPasswordLength
- ComplexityEnabled
- ReversibleEncryptionEnabled
The ComplexityEnabled and MinPasswordLength properties are related. The Native Safety Coverage software offers the next explanations:
ComplexityEnabled: if enabled,
- the passwords cannot include samAccountName or displayName
- passwords should be a minimum of 6 characters lengthy
- passwords should include sure characters (a minimum of one character from every of three of the 4 classes)
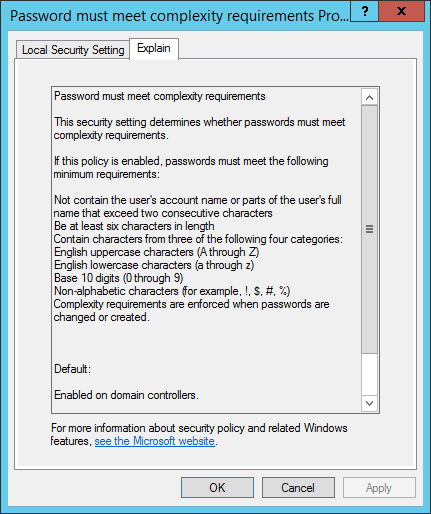
MinPasswordLength: Minimal size of passwords
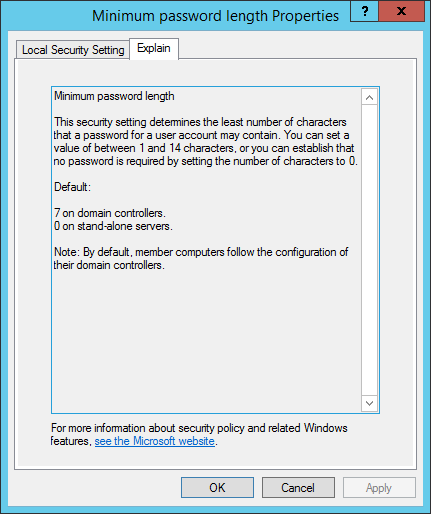
Extra details about right here: https://docs.microsoft.com/en-us/previous-versions/home windows/it-pro/windows-server-2008-R2-and-2008/hh994560(v=ws.10)
The PasswordHistoryCount additionally performs a task, as when a brand new password is generated, it’s not potential to test whether or not this password has been used earlier than (inside the specified variety of previous passwords).
PasswordHistoryCount: Variety of used passwords to be saved in AD. They have to not be reused by the person).
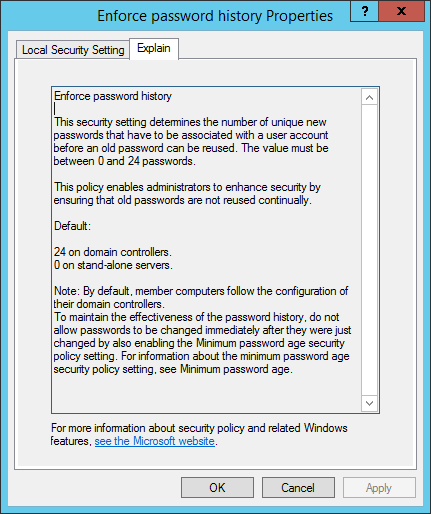
For extra data, go to: https://docs.microsoft.com/en-us/previous-versions/home windows/it-pro/windows-server-2008-R2-and-2008/hh994571(v=ws.10)
Studying the Password Coverage with PowerShell
The CmdLet Get-ADDefaultDomainPasswordPolicy can be utilized to simply learn the area’s password coverage.
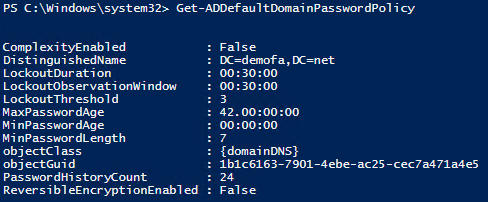
Different attributes resembling LockoutDuration, LockoutObservationWindow and LockoutThreshold are listed right here, which could be discovered within the Native Safety Coverage software underneath Account Lockout Coverage.
The CmdLet Set-ADDefaultDomainPasswordPolicy can be utilized to vary the assorted properties utilizing PowerShell.
First the related parameters are learn out:
|
$coverage = Get–ADDefaultDomainPasswordPolicy $complexity = $coverage.ComplexityEnabled <span class=“crayon-sy”>$<span class=“crayon-v”>minLength</span> <span class=“crayon-o”>=</span> $<span class=“crayon-v”>coverage</span>.<span class=“crayon-i”>MinPasswordLength</span> </span> |
Relying on the complexity set, the era algorithms are utilized, which could be personalized as desired. We present right here a potential instance:
|
if($complexity){ Write–Host(“Komplexes Passwort wird generiert:”) –ForegroundColor Yellow # Komplexe Passwort-Generierung $password = Get–RandomCharacters –size ($minLength – 3) –characters ‘abcdefghijklmnopqrstuvwxyzß’ $password += Get–RandomCharacters –size 1 –characters ‘ABCDEFGHIJKLMNOPQRSTUVWXYZ’ $password += Get–RandomCharacters –size 1 –characters ‘1234567890’ $password += Get–RandomCharacters –size 1 –characters ‘!?:;,.”§$%&amp;/|()[]{}&lt;&gt;@#*-=+~^_’ $password = Scramble–String $password }else{ Write–Host(“Einfaches Passwort wird generiert:”) –ForegroundColor Yellow # Einfach Passwort-Generierung $password = Get–RandomCharacters –size $minLength –characters ‘abcdefghiklmnoprstuvwxyz’ } |
![]()
![]()
As described within the article “PowerShell – Generate random password based on your individual specs” (at the moment solely accessible in German), the next capabilities are used for this objective:
|
perform Get–RandomCharacters($size, $characters) { $random = 1..$size | ForEach–Object { Get–Random –Most $characters.size } $non-public:ofs=“” return [String]$characters[$random] }
perform Scramble–String([string]$inputString) Get–Random –Rely $characterArray.Size $outputString = –be a part of $scrambledStringArray return $outputString
|
Since we’re coping with a randomly generated password, we didn’t test whether or not the samAccountName and displayName of the person are included within the password. Nevertheless, if the password is entered manually, a test is helpful:
|
$samAccountName = “person.take a look at” $displayName = “Take a look at Consumer”
if (($samAccountName) –and ($password –match $samAccountName)) { Write–Host(“Passwort enthält samAccountName des Customers”) –ForegroundColor Crimson }
if ($displayName) { $elements = $displayName.Break up(“,.-,_ #`t”) foreach ($half in $elements) { if (($half) –and ($password –match $half)) { Write–Host(“Passwort enthält Teile des displayName des Customers”) –ForegroundColor Crimson break } } } |
![]()
Since it’s not potential to test the password historical past, the exceptions needs to be caught when setting the password for the person. On this means you may generate a brand new password if crucial.
|
strive{ # …Code… } catch [Microsoft.ActiveDirectory.Management.ADPasswordComplexityException]{ $strException = $_.Exception.Message Write–Host(“Passwort entsprich nicht den Richtlinien; Fehler: “ + $strException) –ForegroundColor Crimson } catch{ $strException = $_.Exception.Message Write–Host(“Fehler: “ + $strException) –ForegroundColor Crimson } |
![]()
Keep away from password generator changes – the entire script
Lastly, right here is the entire script to keep away from password generator changes:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
perform Get–RandomCharacters($size, $characters) { $random = 1..$size | ForEach–Object { Get–Random –Most $characters.size } $non-public:ofs=“” return [String]$characters[$random] }
perform Scramble–String([string]$inputString) Get–Random –Rely $characterArray.Size $outputString = –be a part of $scrambledStringArray return $outputString
$coverage = Get–ADDefaultDomainPasswordPolicy $complexity = $coverage.ComplexityEnabled $minLength = $coverage.MinPasswordLength strive{ if($complexity){ Write–Host(“Komplexes Passwort wird generiert:”) –ForegroundColor Yellow # Komplexe Passwort-Generierung $password = Get–RandomCharacters –size ($minLength – 3) –characters ‘abcdefghijklmnopqrstuvwxyzß’ $password += Get–RandomCharacters –size 1 –characters ‘ABCDEFGHIJKLMNOPQRSTUVWXYZ’ $password += Get–RandomCharacters –size 1 –characters ‘1234567890’ <code> $password += Get–RandomCharacters –size 1</code> –characters ‘!?:;,.”§$%&/|()[]{}<>@#*-=+~^_’ <code> </code> <code>$password = Scramble–String $password }else{
Write–Host(“Einfaches Passwort wird generiert:”) –ForegroundColor Yellow # Einfach Passwort-Generierung $password = Get–RandomCharacters –size $minLength </code>–characters ‘abcdefghiklmnoprstuvwxyz’ } Set–ADAccountPassword –Identification $samAccountName –Reset –NewPassword (ConvertTo–SecureString –AsPlainText –String $password –Power) } catch [Microsoft.ActiveDirectory.Management.ADPasswordComplexityException]{ $strException = $_.Exception.Message Write–Host(“Passwort entsprich nicht den Richtlinien; Fehler: “ + $strException) –ForegroundColor Crimson } catch{ $strException = $_.Exception.Message Write–Host(“Fehler: “ + $strException) –ForegroundColor Crimson } |
Conclusion
Within the article “PowerShell – Generate random password based on personal specs” (at the moment solely accessible in German) we introduced a technique to create passwords with PowerShell. This script will also be utilized in our identification & entry administration resolution FirstWare IDM-Portal, as described. If the password coverage within the firm adjustments now, this script doesn’t essentially must be tailored if the area’s password coverage is noticed from the outset. The passwords will then all the time be generated primarily based on the present coverage.
For non-IT staff who’re administrating, this implies no change. For instance, if the HR division creates a brand new person in AD, the modified password generator script is routinely loaded.
FirstAttribute AG – Identification Administration & IAM Cloud Providers
We help you along with your AD and Azure AD / Microsoft 365 Identification Administration.
Did this aid you? Share it or go away a remark:
Article created: 08.06.2021


