1. Introduction
The first objective of DevSecOps is to foster a tradition of shared duty, collaboration, and steady enchancment. By incorporating safety from the very starting and all through the software program growth lifecycle, organizations can proactively deal with vulnerabilities and make sure the resilience of their purposes and methods.
DevSecOps, quick for Improvement, Safety, and Operations, is an modern method to software program growth that emphasizes integrating safety practices and rules into each part of the software program growth lifecycle. It represents a elementary shift in how organizations historically method software program growth by prioritizing safety from the very starting and integrating it seamlessly into the event course of.DevSecOps goals to interrupt down the silos between growth, safety, and operations groups, fostering collaboration and shared duty all through the software program growth course of. By adopting this method, organizations can deal with safety issues proactively, reduce vulnerabilities, and ship safer and resilient software program options. The advantages of adopting a DevSecOps method are quite a few. It permits organizations to reply extra successfully to the always evolving menace panorama, cut back the time required to detect and mitigate safety points, and finally ship safer and dependable software program merchandise. Furthermore, by integrating safety into the event course of, organizations can obtain higher alignment between safety and enterprise aims, resulting in enhanced buyer belief and aggressive benefit.
1.1 Understanding DevSecOps: Combining Improvement, Safety, and Operations
DevSecOps is an method to software program growth that mixes growth (Dev), safety (Sec), and operations (Ops) practices right into a unified and collaborative course of. It goals to combine safety measures and concerns into each stage of the software program growth lifecycle, from design and coding to testing, deployment, and operations. Historically, software program growth processes have usually handled safety as a separate and remoted concern, addressed late within the growth cycle or as an afterthought. This method can result in vulnerabilities and safety points being found too late, inflicting delays, elevated prices, and potential breaches.
DevSecOps, then again, advocates for safety to be an inherent a part of the event course of from the start. It promotes a shift-left mentality, the place safety practices are utilized early on and constantly all through growth. By incorporating safety practices into the DevOps workflow, organizations can proactively determine and deal with safety dangers, cut back vulnerabilities, and make sure that software program is safe by design.
DevSecOps additionally embraces automation and tooling to streamline safety practices, enabling builders to simply incorporate safety controls into their workflows. By offering builders with the required instruments and assets to construct safe code, DevSecOps empowers them to take possession of safety and ensures that safety measures are applied persistently and effectively throughout the software program growth lifecycle.
1.2 Important Themes in DevSecOps
The important thing themes of DevSecOps could be summarized as follows:
| Key Ideas of DevSecOps | Description |
|---|---|
| Collaboration and Shared Duty | DevSecOps emphasizes collaboration and shared duty amongst growth, safety, and operations groups. |
| Shift-Left Safety | DevSecOps promotes the idea of “shifting left” safety, which implies integrating safety practices and concerns early within the software program growth lifecycle. |
| Automation and Tooling | DevSecOps depends on automation instruments to streamline safety practices and cut back guide efforts. |
| Steady Safety Testing | DevSecOps advocates for steady safety testing all through the event lifecycle. |
| Compliance and Governance | DevSecOps promotes integrating safety controls and compliance necessities into the event course of. |
| Danger Administration | DevSecOps emphasizes a risk-based method to safety. |
| Steady Monitoring and Suggestions | DevSecOps advocates for steady monitoring of the software program in manufacturing. |
| Training and Consciousness | DevSecOps acknowledges the significance of schooling and consciousness amongst builders, safety professionals, and different stakeholders. |
By embracing these key themes, organizations can create a tradition of safety and collaboration, enabling them to construct and deploy software program that’s inherently safe, resilient, and aligned with enterprise aims.
1.2.1 Keep away from These Three Errors in Enterprise Organizations
Listed below are three frequent errors to keep away from in enterprise organizations when implementing DevSecOps:
- Lack of Collaboration and Communication: One of many largest errors in DevSecOps implementation is failing to foster collaboration and communication between growth, safety, and operations groups. It’s essential to interrupt down silos and set up common communication channels to make sure that safety concerns are built-in into each stage of the software program growth lifecycle.
- Insufficient Safety Coaching and Consciousness: Neglecting to offer ample safety coaching and consciousness packages to builders and different stakeholders can undermine the effectiveness of DevSecOps. It’s important to teach and empower workforce members with the required information and abilities to determine and deal with safety points. A scarcity of safety consciousness can result in the introduction of vulnerabilities and weak safety practices in software program growth processes.
- Inadequate Automation and Tooling: One other mistake is just not investing in automation and applicable tooling to assist the DevSecOps workflow. Automation performs an important position in streamlining safety practices, reminiscent of steady integration, steady deployment, and automatic safety testing. With out sufficient automation and tooling, organizations could wrestle to successfully combine safety into their growth pipelines and detect vulnerabilities on time.
These three errors spotlight the significance of collaboration, coaching, consciousness, and automation in profitable DevSecOps implementation inside enterprise organizations. By avoiding these pitfalls, organizations can improve their safety posture and make sure the profitable integration of safety into their software program growth practices.
1.3 The DevSecOps Mission: Unveiling the “Phoenix” Initiative
The 3 ways of safety in DevSecOps speak in regards to the Phoenix challenge. The Phoenix Mission is a ebook written by Gene Kim, Kevin Behr, and George Spafford that explores the challenges and options in remodeling a company’s IT operations. Whereas the ebook doesn’t particularly deal with safety in DevSecOps, we are able to relate the 3 ways of safety in DevSecOps to the rules mentioned in The Phoenix Mission. Right here’s an interpretation:
- Shift-Left Safety and Alignment of Safety Targets: The primary means of safety in DevSecOps aligns with the precept of shifting safety to the left. Equally, in The Phoenix Mission, the primary means focuses on creating an understanding and alignment of targets throughout totally different groups. Within the context of safety, this implies involving safety professionals early within the growth course of and making certain that safety aims and necessities are communicated to all stakeholders.
- Automated Safety Testing and Amplification of Suggestions: The second means of safety in DevSecOps aligns with the idea of automated safety testing. In The Phoenix Mission, the second means emphasizes the necessity for suggestions loops and amplifies suggestions shortly and successfully. Equally, in DevSecOps, organizations implement automated safety testing instruments and processes to offer steady suggestions on the safety of their software program. This helps determine vulnerabilities early, enabling sooner remediation and decreasing safety dangers.
- Steady Monitoring and Response, and Making a Tradition of Studying: The third means of safety in DevSecOps pertains to steady monitoring and response. In The Phoenix Mission, the third means focuses on making a tradition of studying and enchancment. Within the context of safety, this implies establishing steady monitoring mechanisms, reminiscent of real-time safety monitoring and incident response processes, to determine and reply to safety incidents promptly. It additionally includes fostering a tradition of studying from safety occasions, conducting post-incident opinions, and implementing enhancements to stop related incidents sooner or later.
By drawing parallels between the 3 ways of safety in DevSecOps and the rules mentioned in The Phoenix Mission, organizations can perceive the significance of aligning targets, leveraging automation and suggestions loops, and fostering a tradition of studying and enchancment of their safety practices.
1.4 Benefits and Disadvantages of DevSecOps
1.4.1 Benefits
DevSecOps affords a number of benefits for organizations:
- Improved safety posture: DevSecOps integrates safety practices all through the software program growth lifecycle, making certain that safety concerns are addressed early on and constantly. By embedding safety into each stage of growth, organizations can improve their general safety posture and cut back the danger of vulnerabilities and safety breaches.
- Sooner time to market: DevSecOps promotes automation, steady integration, and steady supply (CI/CD) practices. This automation streamlines the event and deployment processes, permitting organizations to launch software program sooner and extra continuously. By integrating safety into these automated processes, safety measures could be applied with out considerably slowing down growth cycles.
- Early detection and mitigation of vulnerabilities: DevSecOps incorporates safety testing and scanning instruments into the event pipeline, enabling the early detection and mitigation of vulnerabilities. Automated safety testing helps determine safety weaknesses, reminiscent of code flaws or misconfigurations, and permits builders to handle them promptly earlier than they turn into extra advanced and costly to repair.
- Elevated collaboration and communication: DevSecOps fosters collaboration between growth, operations, and safety groups. This collaboration improves communication, information sharing, and mutual understanding of every workforce’s necessities and issues. By working collectively, groups can align their efforts towards constructing safe and dependable software program.
- Steady compliance and auditing: Compliance with regulatory requirements and business finest practices is crucial for a lot of organizations. DevSecOps allows steady compliance by integrating compliance checks and audits into the event course of. This method ensures that safety controls and necessities are met persistently, decreasing the hassle and potential disruptions related to compliance assessments.
- Danger discount and mitigation: By addressing safety early within the growth course of, DevSecOps helps mitigate dangers related to software program vulnerabilities and safety breaches. Proactive identification and mitigation of safety points reduce the probability of profitable assaults and potential harm to the group’s fame, monetary stability, and buyer belief.
- Agile and adaptive safety: DevSecOps promotes an agile and adaptive safety mindset. Safety measures could be constantly evaluated, adjusted, and improved primarily based on rising threats, evolving safety requirements, and altering enterprise necessities. This permits organizations to remain resilient and reply successfully to new safety challenges.
1.4.2 Disadvantages
Whereas DevSecOps brings quite a few advantages, there are additionally some potential disadvantages or challenges related to its implementation. Listed below are a couple of disadvantages of DevSecOps:
- Preliminary funding and studying curve: Adopting DevSecOps practices could require an preliminary funding by way of assets, instruments, and coaching. Organizations must allocate time and assets to coach their groups on safety practices, implement new instruments and applied sciences, and set up new processes. This preliminary studying curve and funding is usually a problem for some organizations, particularly these with restricted assets or resistance to alter.
- Integration complexities: Integrating safety practices into the event course of can introduce complexities. Organizations could face challenges in integrating safety instruments and practices seamlessly into their current growth workflows. Compatibility points, configuration challenges, and the necessity to align with totally different growth environments and applied sciences can create further overhead and decelerate the event course of.
- Balancing velocity and safety: DevSecOps goals to allow sooner software program supply whereas making certain safety. Nonetheless, there is usually a potential rigidity between velocity and safety necessities. Putting the correct stability between speedy growth cycles and strong safety measures could be difficult. Organizations want to search out methods to prioritize safety with out inflicting vital delays or compromising the agility and velocity of software program supply.
- Talent gaps and experience: Implementing DevSecOps requires expert personnel who possess experience in each growth and safety domains. Discovering people with a powerful understanding of each areas could be difficult, and organizations could must spend money on coaching or hiring specialised expertise. Bridging the ability gaps between growth and safety groups can take effort and time.
- Cultural and organizational challenges: DevSecOps requires a cultural shift and a collaborative mindset throughout totally different groups, together with builders, operations, and safety professionals. Overcoming organizational silos, fostering efficient communication, and selling a shared duty for safety could be difficult. Resistance to alter and the necessity to align totally different groups with various priorities and views could decelerate the adoption of DevSecOps practices.
- Steady monitoring and upkeep: DevSecOps promotes steady monitoring and upkeep of safety measures all through the software program growth lifecycle. This ongoing effort requires devoted assets and a focus to make sure that safety controls stay efficient, vulnerabilities are promptly addressed, and compliance is maintained. Organizations must allocate assets and set up processes for steady monitoring, upkeep, and updating of safety practices.
2. Embarking on the DevSecOps Journey: A Newbie’s Information
Right here’s an instance of how one can get began with DevSecOps by incorporating safety right into a “Whats up, World!” software:
- Set Up Model Management: Begin by organising a model management system like Git to handle your codebase. Initialize a brand new repository and create a easy “Whats up, World!” software.
- Combine Safety Code Evaluation: Select a safety code evaluation software reminiscent of SonarQube or Snyk. Configure the software to scan your code for potential safety vulnerabilities, coding finest practices, and different points. This may be finished as a part of your CI/CD pipeline or in the course of the growth course of.
- Implement Automated Testing: Create automated safety checks to validate the safety of your software. This may embody testing for frequent vulnerabilities reminiscent of injection assaults, cross-site scripting (XSS), or insecure direct object references (IDOR). Combine these safety checks into your CI/CD pipeline to run them mechanically with every code commit or deployment.
- Containerize Your Utility: Containerization gives an extra layer of safety and portability. Docker is a well-liked alternative for containerization. Containerize your “Whats up, World!” software by making a Dockerfile and packaging your software right into a Docker container.
- Container Picture Scanning: Use container picture scanning instruments like Clair or Anchore to scan your Docker picture for identified vulnerabilities. This helps determine and deal with any safety points throughout the container picture earlier than deployment.
- Steady Monitoring and Logging: Implement steady monitoring and logging practices to realize visibility into the runtime habits of your software. Make the most of instruments like Prometheus, ELK stack (Elasticsearch, Logstash, and Kibana), or Splunk to gather and analyze logs and metrics. Arrange alerts to detect any suspicious actions or security-related occasions.
- Safety Incident Response: Set up a safety incident response course of to deal with any safety incidents or vulnerabilities found. Outline roles and duties, set up communication channels, and doc procedures for figuring out, mitigating, and resolving safety incidents.
- Training and Consciousness: Promote safety schooling and consciousness amongst your growth and operations groups. Conduct safety coaching periods to teach workforce members on safe coding practices, frequent vulnerabilities, and safety finest practices. Encourage a security-first mindset and foster a tradition of steady studying and enchancment.
Keep in mind, it is a fundamental “Whats up, World!” instance, however the rules could be utilized to extra advanced purposes. The secret is to combine safety all through your entire software program growth lifecycle, automate safety practices, and constantly monitor and enhance the safety of your purposes.
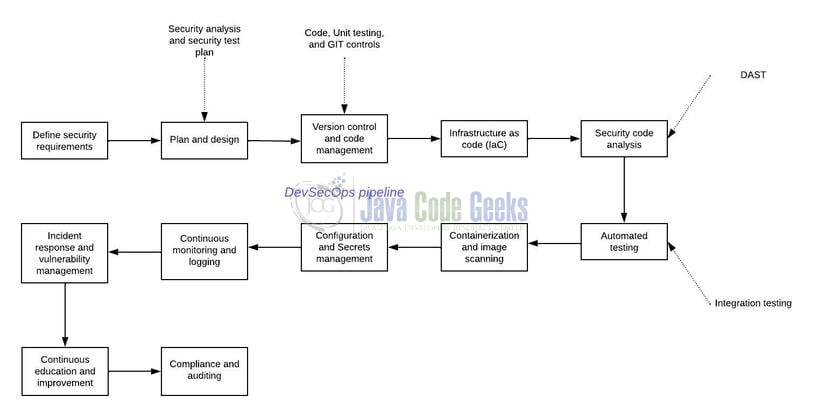
2.1 Growing a DevSecOps Pipeline: Constructing the Bridge
Making a DevSecOps pipeline includes integrating safety practices and instruments into your software program growth lifecycle. Listed below are the important thing steps to create a DevSecOps pipeline:
- Outline Safety Necessities: Determine the safety necessities and aims particular to your software or group. This might embody compliance rules, safety requirements, or business finest practices.
- Plan and Design: Plan and design your DevSecOps pipeline. Contemplate the levels of your pipeline, reminiscent of code growth, testing, deployment, and monitoring. Decide how safety practices and instruments shall be built-in into every stage.
- Model Management and Code Administration: Use a model management system like Git to handle your codebase. Implement branching methods and insurance policies to make sure code integrity and traceability.
- Infrastructure as Code (IaC): Apply Infrastructure as Code rules to outline and handle your infrastructure. Use instruments like Terraform or AWS CloudFormation to automate the provisioning and configuration of infrastructure assets, making certain consistency and safety.
- Safety Code Evaluation: Combine safety code evaluation instruments into your pipeline. Instruments like SonarQube or Snyk can scan your code for potential safety vulnerabilities, coding finest practices, and different points. Arrange automated scans triggered by code commits or pull requests.
- Automated Testing: Implement automated safety testing to validate the safety of your software. This may embody static software safety testing (SAST), dynamic software safety testing (DAST), or software program composition evaluation (SCA) instruments. Embrace safety checks as a part of your steady integration and steady deployment (CI/CD) pipeline.
- Containerization and Picture Scanning: Containerize your software utilizing instruments like Docker or Kubernetes. Scan your container pictures for identified vulnerabilities utilizing instruments like Clair or Anchore earlier than deployment. Automate this course of as a part of your CI/CD pipeline.
- Configuration and Secrets and techniques Administration: Use configuration administration instruments like Ansible or Chef to handle and safe your software configurations. Implement secrets and techniques administration instruments to securely retailer and handle delicate info reminiscent of passwords and API keys.
- Steady Monitoring and Logging: Implement steady monitoring practices to realize real-time visibility into the safety of your software. Make the most of instruments like Prometheus, ELK stack (Elasticsearch, Logstash, and Kibana), or Splunk to gather and analyze logs and metrics. Arrange alerts for security-related occasions.
- Incident Response and Vulnerability Administration: Set up a safety incident response course of to deal with safety incidents or vulnerabilities found. Outline roles, duties, and communication channels. Implement vulnerability administration practices to determine, prioritize, and remediate vulnerabilities.
- Steady Training and Enchancment: Promote safety schooling and consciousness amongst your groups. Present coaching on safe coding practices, frequent vulnerabilities, and safety finest practices. Foster a tradition of steady studying and enchancment by conducting security-related retrospectives and implementing classes realized.
- Compliance and Auditing: Guarantee your DevSecOps pipeline complies with related rules and requirements. Conduct common audits to evaluate the effectiveness of your safety practices and deal with any compliance gaps.
Do not forget that every group’s DevSecOps pipeline will range primarily based on particular necessities and expertise stack. It’s necessary to constantly assess and refine your pipeline to adapt to evolving safety threats and finest practices.
2.2 Choosing Safety Instruments and Applied sciences: Making Knowledgeable Decisions
When selecting safety instruments and applied sciences for DevSecOps, it’s necessary to think about your particular necessities, the character of your purposes, and the general targets of your DevSecOps initiative. Listed below are some elements to think about when choosing safety instruments and applied sciences:
- Complete Safety Protection: Search for instruments that provide a variety of safety capabilities to cowl varied features of software safety, reminiscent of code evaluation, vulnerability scanning, menace detection, entry administration, and compliance.
- Integration with DevOps Toolchain: Make sure that the safety instruments can seamlessly combine together with your current DevOps toolchain, together with model management methods, CI/CD platforms, and deployment automation instruments. The combination allows clean collaboration and automation throughout your entire growth and deployment lifecycle.
- Automation and Steady Monitoring: Select instruments that assist automation and steady monitoring to offer real-time insights into the safety posture of your purposes. Automated safety testing, vulnerability scanning, and log evaluation assist determine and deal with safety points at an early stage.
- Scalability and Efficiency: Contemplate the scalability and efficiency necessities of your purposes and consider whether or not the safety instruments can deal with the anticipated workload with out inflicting efficiency bottlenecks or delays within the growth and deployment processes.
- Open Supply or Business: Resolve whether or not to make use of open-source safety instruments or go for business options. Open-source instruments usually provide flexibility and group assist, whereas business instruments could present further options, assist, and devoted customer support.
- Vendor Repute and Help: Analysis the fame and monitor document of the software distributors. Search for distributors with an excellent fame, established buyer base, and optimistic opinions. Additionally, contemplate the extent of assist they supply, together with documentation, coaching, and buyer assist channels.
- Compliance and Regulatory Necessities: In case your purposes must adjust to particular rules or requirements, make sure that the safety instruments align with these necessities. Search for instruments that present compliance checks, reporting, and auditing capabilities that can assist you meet the required safety requirements.
- Consumer-Pleasant Interface and Usability: Consider the consumer interface and value of the safety instruments. A user-friendly interface simplifies configuration, monitoring, and evaluation, making it simpler on your growth and safety groups to collaborate successfully.
- Value Concerns: Contemplate the prices related to the safety instruments, together with licensing charges, upkeep, and ongoing assist. Consider the worth offered by the instruments about their value and make sure that they match inside your funds constraints.
- Group and Ecosystem: Assess the scale and exercise of the software’s consumer group and ecosystem. A vibrant group can present beneficial assets, plugins, and integrations that improve the performance and usefulness of safety instruments.
Keep in mind to prioritize the instruments that align together with your particular safety targets and necessities. It’s additionally really useful to conduct proof-of-concept evaluations or trials to evaluate the suitability of the instruments inside your group’s surroundings earlier than making a remaining choice.
2.2.1 Totally different code scanning and safety instruments
- SAST Instruments (Static Utility Safety Testing): These instruments, reminiscent of SonarQube and Veracode, analyze the supply code or compiled code of an software to determine potential safety vulnerabilities and coding errors.
- DAST Instruments (Dynamic Utility Safety Testing): OWASP ZAP and Burp Suite are examples of DAST instruments. They consider the safety of working purposes by sending varied requests and analyzing the responses, serving to to determine vulnerabilities which will come up throughout runtime.
- IAST Instruments (Interactive Utility Safety Testing): IAST instruments like Distinction Safety and Synopsys present real-time monitoring of purposes throughout runtime. By instrumenting the code, they detect vulnerabilities and supply insights into the particular elements inflicting the problems.
- SCA Instruments (Software program Composition Evaluation): SCA instruments like Black Duck and WhiteSource look at the open-source elements utilized in an software’s codebase. They determine any identified vulnerabilities or license compliance points related to the third-party libraries and dependencies.
2.2.2 Comparability between distinction code scanning and safety instruments
| Device | Benefits | Disadvantages |
|---|---|---|
| Static Utility Safety Testing |
|
|
| Dynamic Utility Safety Testing |
|
|
| Interactive Utility Safety Testing |
|
|
| Software program Composition Evaluation |
|
|
3. Core Practices in DevSecOps Implementation
DevSecOps practices discuss with the combination of safety practices and rules into the DevOps method. It goals to make sure that safety is handled as an integral a part of the software program growth and deployment course of, fairly than an afterthought. By incorporating safety early on and all through the event lifecycle, DevSecOps practices assist organizations construct safe and resilient methods. Listed below are some key DevSecOps practices:
| Key Practices in DevSecOps | Description |
|---|---|
| Shift-Left Safety | DevSecOps emphasizes shifting safety practices and concerns to the left, that means safety is integrated early within the growth course of. This includes involving safety professionals from the start, conducting safety opinions, menace modeling, and integrating safety instruments into the event surroundings. |
| Safety Automation | Automation performs an important position in DevSecOps practices. By automating safety processes, reminiscent of code evaluation, vulnerability scanning, and compliance checks, organizations can determine safety points early and deal with them effectively. Automation additionally helps guarantee consistency and repeatability in safety practices. |
| Steady Safety Testing | Steady safety testing is a core apply in DevSecOps. It includes integrating safety testing, reminiscent of static software safety testing (SAST), dynamic software safety testing (DAST), and software program composition evaluation (SCA), into the CI/CD pipeline. This permits safety vulnerabilities and weaknesses to be detected and addressed quickly as a part of the event and deployment course of. |
| Infrastructure as Code (IaC) Safety | In DevSecOps, safety is prolonged past software code to incorporate infrastructure. Infrastructure as Code (IaC) practices permit organizations to outline and handle their infrastructure by means of code. By incorporating safety controls and finest practices into IaC templates and scripts, organizations can guarantee constant and safe infrastructure provisioning. |
| Safe Configuration Administration | Safe configuration administration includes implementing safe configurations for all elements of the appliance stack, together with servers, databases, and community units. By following safety configuration tips and repeatedly auditing and updating configurations, organizations can mitigate safety dangers. |
| Steady Monitoring and Incident Response | Steady monitoring is essential to determine and reply to safety incidents promptly. DevSecOps encourages the implementation of real-time safety monitoring, log evaluation, and menace intelligence to detect and reply to safety occasions. Incident response plans and processes ought to be established to deal with safety incidents successfully. |
| Safety Consciousness and Training | Constructing a security-conscious tradition is important in DevSecOps. Organizations ought to spend money on safety consciousness and teaching programs to coach builders, operations groups, and different stakeholders on safe coding practices, safety threats, and finest practices. Steady studying and information sharing assist foster a security-first mindset. |
| Compliance and Governance | DevSecOps practices ought to align with related rules, business requirements, and compliance necessities. Organizations must combine compliance checks, reporting, and auditing capabilities into their processes to make sure adherence to safety requirements and rules. |
| Collaboration and Communication | Efficient collaboration and communication between growth, operations, and safety groups are important in DevSecOps. Groups ought to work collectively to share info, determine dangers, and implement safety controls. Collaboration instruments and practices ought to be adopted to facilitate seamless communication and cooperation. |
By embracing these DevSecOps practices, organizations can construct safe, scalable, and resilient methods whereas sustaining the velocity and agility offered by the DevOps method.
3.1 Enhancing DevSecOps with Extra Practices
Along with the core practices of integrating safety into the software program growth course of, a number of further practices can improve the effectiveness of DevSecOps:
| Safety Practices | Description |
|---|---|
| Menace modeling | Conducting menace modeling helps determine potential safety threats and vulnerabilities within the system early on. This apply includes analyzing the system structure, figuring out potential assault vectors, and prioritizing safety measures primarily based on the recognized dangers. Menace modeling helps in designing and implementing applicable safety controls. |
| Safe coding tips | Establishing and imposing safe coding tips is essential for constructing safe software program. These tips present builders with finest practices for writing safe code, reminiscent of enter validation, output encoding, and safe authentication mechanisms. Common code opinions and automatic code evaluation instruments might help guarantee adherence to those tips. |
4. Exploring Totally different DevSecOps Instruments
4.1 Configuration Administration Instruments
Configuration administration is an important side of recent software program growth and IT operations. It includes managing and controlling the configuration of software program methods, infrastructure, and purposes all through their lifecycle. Configuration administration instruments play a crucial position in automating and simplifying this course of.
Configuration administration instruments allow organizations to standardize and automate the deployment, configuration, and upkeep of software program and infrastructure elements. These instruments present a centralized platform for managing configuration information, settings, and parameters throughout totally different environments, making certain consistency and reliability.
One of many key advantages of configuration administration instruments is their skill to implement desired states. They permit groups to outline and preserve the specified configuration of methods and mechanically apply any essential adjustments to make sure the methods align with the specified state. This helps in decreasing configuration drift, the place methods deviate from their meant configuration over time.
These instruments additionally facilitate infrastructure as code (IaC) practices, the place infrastructure and configuration are outlined and managed utilizing code. By treating infrastructure as code, organizations can model management their configuration, monitor adjustments, and reproduce environments precisely.
Configuration administration instruments provide a spread of options and capabilities, together with declarative configuration languages, dependency administration, automated provisioning, and orchestration. They combine with varied platforms, cloud suppliers, and working methods, enabling organizations to handle advanced and numerous environments seamlessly.
Some common configuration administration instruments embody Ansible, Puppet, and Chef. These instruments present strong options for automating configuration administration duties, enabling groups to scale their operations, enhance effectivity, and cut back guide errors.
4.1.1 Ansible
Ansible is an open-source automation platform that simplifies the administration and configuration of methods and purposes. It makes use of a declarative language referred to as YAML (YAML Ain’t Markup Language) to outline the specified state of infrastructure and carry out duties throughout a number of machines. Right here’s a pattern code snippet that demonstrates the usage of Ansible to put in and configure an online server:
- title: Set up and configure Apache net server
hosts: webserver
turn into: true
duties:
- title: Set up Apache bundle
apt:
title: apache2
state: current
- title: Allow Apache service
service:
title: apache2
enabled: true
state: began
- title: Copy customized index.html file
copy:
src: /path/to/index.html
dest: /var/www/html/index.html
proprietor: root
group: root
mode: 0644
4.1.2 Puppet
Puppet is a configuration administration software that automates the provisioning, configuration, and administration of methods. It makes use of a declarative language referred to as Puppet DSL to outline the specified state of the infrastructure. Right here’s a pattern Puppet manifest that installs and configures an online server:
node 'webserver' {
bundle { 'apache2':
guarantee => put in,
}
service { 'apache2':
guarantee => working,
allow => true,
require => Package deal['apache2'],
}
file { '/var/www/html/index.html':
guarantee => file,
supply => '/path/to/index.html',
proprietor => 'root',
group => 'root',
mode => '0644',
require => Package deal['apache2'],
notify => Service['apache2'],
}
}
4.1.3 Chef
Chef is a strong configuration administration and automation software that permits you to outline infrastructure as code. It makes use of a domain-specific language (DSL) to explain the specified state of methods and automate the configuration course of. Right here’s a pattern Chef recipe that installs and configures an online server:
bundle 'apache2' do motion :set up finish service 'apache2' do motion [:enable, :start] finish cookbook_file '/var/www/html/index.html' do supply 'index.html' proprietor 'root' group 'root' mode '0644' motion :create notifies :restart, 'service[apache2]' finish
4.2 Steady Integration and Supply Instruments
Steady Integration and Supply (CI/CD) has turn into an important apply in trendy software program growth, enabling groups to ship high-quality software program sooner and extra effectively. CI/CD instruments play an important position in automating the construct, testing, and deployment processes, making certain clean and dependable software program supply pipelines.
CI/CD instruments facilitate the combination of code adjustments from a number of builders right into a shared repository, the place automated builds and checks are triggered. These instruments allow groups to catch integration points early, determine bugs, and make sure that the codebase stays steady. By constantly integrating code adjustments, builders can collaborate successfully and detect and resolve points extra effectively.
Steady Supply (CD) takes CI a step additional by automating the deployment course of. CD instruments allow organizations to bundle, deploy, and launch software program purposes persistently throughout totally different environments. By automating the deployment course of, groups can cut back guide errors, guarantee consistency, and obtain sooner time-to-market.
CI/CD instruments provide a variety of options to assist the event and supply lifecycle. They usually present capabilities reminiscent of code repository integration, construct automation, automated testing, artifact administration, and deployment orchestration. These instruments combine with common model management methods like Git and assist varied programming languages and frameworks.
One of many key advantages of CI/CD instruments is the power to automate your entire software program supply pipeline, from supply code administration to manufacturing deployment. They supply visibility into the construct and deployment course of, permitting groups to trace adjustments, monitor progress, and determine bottlenecks. With automated testing and high quality checks, these instruments assist preserve code high quality and make sure that solely dependable and well-tested software program is launched.
4.2.1 Jenkins
Jenkins is an open-source automation server that allows steady integration and steady supply (CI/CD) of software program tasks. It gives a variety of plugins and integrations, permitting for straightforward customization and extensibility. Right here’s an instance of a Jenkins pipeline script that builds and deploys an online software:
pipeline {
agent any
levels {
stage('Construct') {
steps {
sh 'npm set up'
}
}
stage('Take a look at') {
steps {
sh 'npm take a look at'
}
}
stage('Deploy') {
steps {
sh 'npm run deploy'
}
}
}
}
4.2.2 GitLab CI/CD
GitLab CI/CD is a built-in steady integration and steady supply platform offered by GitLab. It permits you to outline CI/CD pipelines utilizing a configuration file referred to as .gitlab-ci.yml. Right here’s an instance .gitlab-ci.yml file that builds and deploys an online software:
levels:
- construct
- take a look at
- deploy
construct:
stage: construct
script:
- npm set up
take a look at:
stage: take a look at
script:
- npm take a look at
deploy:
stage: deploy
script:
- npm run deploy
4.2.3 CircleCI
CircleCI is a cloud-based CI/CD platform that automates the construct, take a look at, and deployment processes. It gives a easy and intuitive configuration file referred to as config.yml to outline the pipeline. Right here’s an instance config.yml file for constructing and deploying an online software:
model: 2.1
jobs:
build-and-deploy:
docker:
- picture: node:newest
steps:
- checkout
- run:
title: Construct
command: npm set up
- run:
title: Take a look at
command: npm take a look at
- run:
title: Deploy
command: npm run deploy
4.3 Containerization and Orchestration Instruments
Containerization and orchestration have turn into elementary pillars of recent software deployment and administration. Containerization instruments allow organizations to bundle purposes and their dependencies into light-weight, moveable containers, whereas orchestration instruments automate the deployment, scaling, and administration of those containers. Collectively, they revolutionize software program supply, scalability, and resilience. Some common containerization and orchestration instruments embody:
4.3.1 Docker
Docker is an open-source platform that permits you to automate the deployment and administration of purposes inside light-weight, remoted containers. It gives a solution to bundle purposes and their dependencies into moveable containers that may run persistently throughout totally different environments. Right here’s an instance of utilizing Docker to run an online server:
docker run -d -p 80:80 nginx – This command pulls the Nginx picture from the Docker registry and runs it in a container, mapping port 80 of the host to port 80 of the container. This permits the Nginx net server to be accessed on the host machine.
4.3.2 Kubernetes
Kubernetes is an open-source container orchestration platform that automates the deployment, scaling, and administration of containerized purposes. It gives a extremely versatile and resilient structure to run and handle containers throughout clusters of machines. Right here’s an instance of deploying an software on Kubernetes:
kubectl create deployment my-app --image=myapp:1.0 – This command creates a deployment referred to as “my-app” utilizing the container picture “myapp:1.0”. Kubernetes will mechanically schedule and handle the appliance pods primarily based on the specified state outlined within the deployment.
4.3.3 OpenShift
OpenShift is a container software platform that builds on high of Kubernetes. It gives an enterprise-ready, absolutely managed container platform with further options and capabilities for software growth, deployment, and scaling. Right here’s an instance of deploying an software on OpenShift:
oc new-app myapp:1.0 – This command creates a brand new software referred to as “myapp” utilizing the container picture “myapp:1.0” and mechanically units up the required assets, reminiscent of deployment configurations, companies, and routes, to run the appliance on OpenShift.
4.4 Safety Info and Occasion Administration (SEM) Instruments
SIEM instruments present a centralized platform for accumulating, analyzing, and correlating safety occasion information from varied sources, reminiscent of logs, community units, purposes, and endpoints. By aggregating and analyzing this information, SIEM instruments allow organizations to detect and reply to safety incidents in actual time, in addition to proactively determine potential threats.
The first objective of SIEM instruments is to offer complete visibility into a company’s safety posture. They assist safety groups monitor and analyze logs and occasions from numerous sources, determine patterns, and generate actionable insights. SIEM instruments use superior correlation algorithms, anomaly detection, and menace intelligence feeds to determine potential safety incidents, reminiscent of unauthorized entry makes an attempt, malware infections, or information breaches.
SIEM instruments provide a variety of options and capabilities. They supply real-time occasion monitoring, log administration, and log evaluation capabilities. They will mechanically mixture and normalize log information from totally different sources, making it simpler to determine patterns and detect safety occasions. SIEM instruments additionally present alerting and notification mechanisms to make sure that safety groups can reply promptly to potential threats or incidents.
One other crucial side of SIEM instruments is their reporting and compliance capabilities. They assist organizations meet regulatory necessities by offering pre-built stories and facilitating audit processes. SIEM instruments can generate compliance stories, monitor consumer actions, and supply proof of safety controls, thereby supporting organizations in demonstrating adherence to business requirements and rules.
Some common SIEM instruments embody:
4.4.1 Splunk
Splunk is a strong platform used for monitoring, looking, analyzing, and visualizing machine-generated information. It collects and indexes information from varied sources, together with logs, occasions, and metrics, and gives real-time insights and actionable intelligence. Splunk’s options embody highly effective search capabilities, information visualization, alerting, and machine studying. It helps organizations achieve beneficial insights from their information and allows efficient troubleshooting, safety monitoring, and enterprise intelligence.
4.4.2 ELK Stack (Elasticsearch, Logstash, Kibana)
The ELK Stack, now often known as the Elastic Stack, is a mix of three open-source instruments:
Elasticsearch: Elasticsearch is a extremely scalable and distributed search and analytics engine. It shops and indexes information in close to real-time, permitting for quick and environment friendly search, evaluation, and retrieval of structured and unstructured information.
Logstash: Logstash is a knowledge assortment and processing pipeline. It helps in ingesting and parsing information from varied sources, reminiscent of logs, metrics, and occasion streams. Logstash allows information transformation and enrichment earlier than sending it to Elasticsearch for indexing and evaluation.
Kibana: Kibana is a knowledge visualization and exploration software that works along with Elasticsearch. It gives a web-based interface for querying and visualizing information saved in Elasticsearch. Kibana affords highly effective visualization choices, dashboards, and search capabilities, enabling customers to interactively discover and achieve insights from their information.
Collectively, the ELK Stack gives a complete answer for log administration, log evaluation, and information visualization. It’s broadly used for monitoring system and software logs, analyzing metrics, and producing significant visualizations and dashboards.
4.4.3 IBM QRadar
IBM QRadar is a safety info and occasion administration (SIEM) platform that helps organizations detect and reply to safety threats. It collects and correlates log information from varied sources, together with community units, servers, and purposes, to offer complete visibility into safety occasions. QRadar affords options like real-time menace detection, incident response workflows, log evaluation, and safety occasion correlation. It makes use of superior analytics and machine studying algorithms to determine potential safety incidents and gives actionable insights to safety analysts.
IBM QRadar is broadly used for safety monitoring, menace detection, and compliance reporting, serving to organizations proactively determine and mitigate safety dangers.
5. Open-Supply Instruments and Initiatives
| Device/Mission Identify | Key Options | Major Use Case |
|---|---|---|
| Jenkins | Intensive plugin ecosystem, distributed builds straightforward integration with model management methods. | Constructing, testing, and deploying purposes in a steady integration and supply pipeline. |
| Ansible | Agentless structure, declarative language, and a big community-driven library of modules. | Configuration administration, software deployment, and infrastructure orchestration. |
| Docker | Containerization, portability, and environment friendly useful resource utilization. | Utility deployment, microservices structure, container orchestration. |
| Kubernetes | Scalability, excessive availability, self-healing capabilities, and repair discovery. | Container orchestration, managing advanced microservices architectures. |
| Git | Branching, merging, model historical past, collaboration. | Supply code administration and collaboration amongst builders. |
| Prometheus | Time-series database, versatile question language, in depth integrations. | Monitoring infrastructure, purposes, and companies. |
| Grafana | Customizable dashboards, a variety of information supply integrations, and alerting capabilities. | Monitoring, observability, and visualization of metrics and logs. |
| Terraform | Declarative language, multi-cloud assist, dependency administration. | Infrastructure provisioning and administration in a cloud surroundings. |
| Nagios | Monitoring host and repair availability, alerting, and extensibility by means of plugins. | Monitoring and alerting for infrastructure and purposes. |
| Gradle | Dependency administration, multi-project builds, extensible plugin system. | Constructing and packaging software program tasks. |
6. Assets for studying DevSecOps
Listed below are some assets for studying DevSecOps.