Home windows LAPS is a Home windows characteristic that means that you can mechanically set and backup native administrator passwords of your domain-joined gadgets. LAPS (Native Administrator Password Resolution), creates a singular and random password for every machine in your community and shops it within the Lively Listing or Azure Lively Listing.
Home windows LAPS is the successor of the legacy Microsoft LAPS, which has been obtainable for the previous years. The brand new Home windows LAPS comes with extra options and is now constructed into Home windows 10 and 11. So we don’t want to put in a consumer on the computer systems anymore.
On this article, we’re going to check out the distinction between Microsoft LAPS and Home windows LAPS, easy methods to set up and configure the brand new LAPS, and easy methods to migrate from legacy LAPS to Home windows LAPS.
What’s Home windows LAPS?
You possibly can simply change the password of your area administrator account, however what in regards to the native administrator account? The password of the native admin account is usually set throughout set up, however you possibly can’t simply change it on all computer systems. That is the place Home windows LAPS is available in. LAPS stands for Native Administrator Password Resolution.
With LAPS we will mechanically set distinctive native administrator passwords on every pc, that are saved within the Azure Lively Listing or in your native Lively Listing. The password is mechanically modified each 30 days by default. Home windows LAPS may also be used to handle and again up the DSRM (Listing Companies Restore Mode) password of your Lively Listing.
Microsoft LAPS vs Home windows LAPS
Home windows LAPS is the successor of Microsoft LAPS, which has been obtainable for a few years. So what are the variations between the 2 variations? A very powerful change is that the brand new model is constructed into Home windows. Because of this we don’t have to put in an MSI anymore on the purchasers. However there are extra benefits:
- Retailer password in Azure AD – Simpler to retrieve password
- Password Historical past – View earlier passwords, helpful for restoration eventualities
- Encrypt passwords – Improves safety in native Lively Listing
- Mechanically rotate password – Reset password after the account is used
- View with Microsoft Graph – You possibly can retrieve the passwords with Microsoft Graph
- DSRM Password Backups – Safe and rotate the area controller restoration password
- New PowerShell Module – Provides you extra management by way of PowerShell
- Devoted occasion log – Makes it simpler to troubleshoot points
Necessities
To make use of Home windows LAPS you’ll need to guarantee that your computer systems and servers have the newest safety replace, from April 11, 2023, put in. The next working methods are supported:
- Home windows 11 Professional, EDU, and Enterprise
- Home windows 10 Professional, EDU, and Enterprise
- Home windows Server 2022
- Home windows Server 2019
Make it possible for all of your area controllers are absolutely up to date earlier than you begin with the set up.
How one can Set up Home windows LAPS
In case your gadgets are managed with Intune, then it’s really helpful to roll out LAPS utilizing the Home windows LAPS configuration service suppliers. While you don’t use Intune, then you possibly can nonetheless deploy LAPS, utilizing your native Lively Listing.
I’ll clarify each strategies, beginning with the native Lively Listing.
Deploy LAPS on native Lively Listing
This methodology can be utilized when you could have a whole on-premise atmosphere and for hybrid environments the place your native Lively Listing is synced with Azure Lively Listing.
Step 1 – Prolong AD Schema
Step one is to increase the Lively Listing schema. We do that on one area controller, which then will mechanically sync the brand new schema to the opposite area controllers in your forest.
To replace the AD Schema, open PowerShell (Admin) on the area controller and run the next command:
Replace-LapsADSchema
Press A (Sure to all) on the query if you wish to proceed. Should you get an error working the Replace-LapsADSchema command, then test the FAQ on the finish of the article for attainable options.
We are able to confirm the Lively Listing schema extension by opening a pc object within the Lively Listing. You’ll now see the brand new LAPS tab.
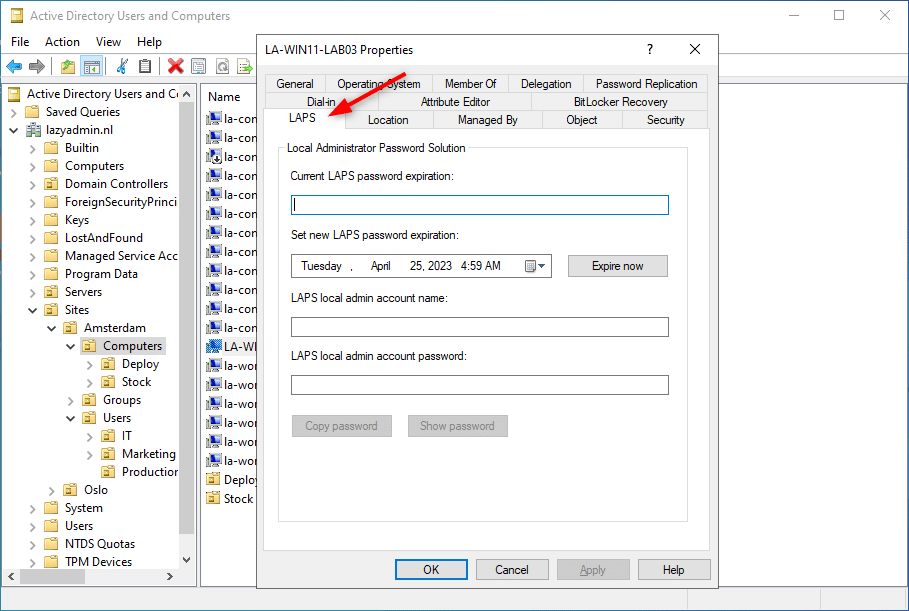
Step 2 – Set Permissions
The computer systems must have permission to replace their password within the Lively Listing. We do that by setting inheritable permissions on the OU of the computer systems with the assistance of the Set-LapsADComputerSelfPermission cmdlet in PowerShell.
We might want to specify the OU identify, if the identify isn’t distinctive in your Lively Listing, then you’ll need to specify the DistinguishedName.
Set-LapsADComputerSelfPermission -Id "Computer systems" # Or with the total distinguishedName: Set-LapsADComputerSelfPermission -Id "OU=Computer systems,OU=Amsterdam,OU=Websites,DC=lazyadmin,DC=nl"
Step 3 – Configure LAPS Group Insurance policies
To configure LAPS we might want to create a brand new Group Coverage.
- Open the Group Coverage Administration on the area controller
- Create a brand new Pc Coverage (CPO_LAPS) in your pc OU
- Edit the brand new coverage and navigate to Pc Configuration > Insurance policies > Administrative Templates > System > LAPS
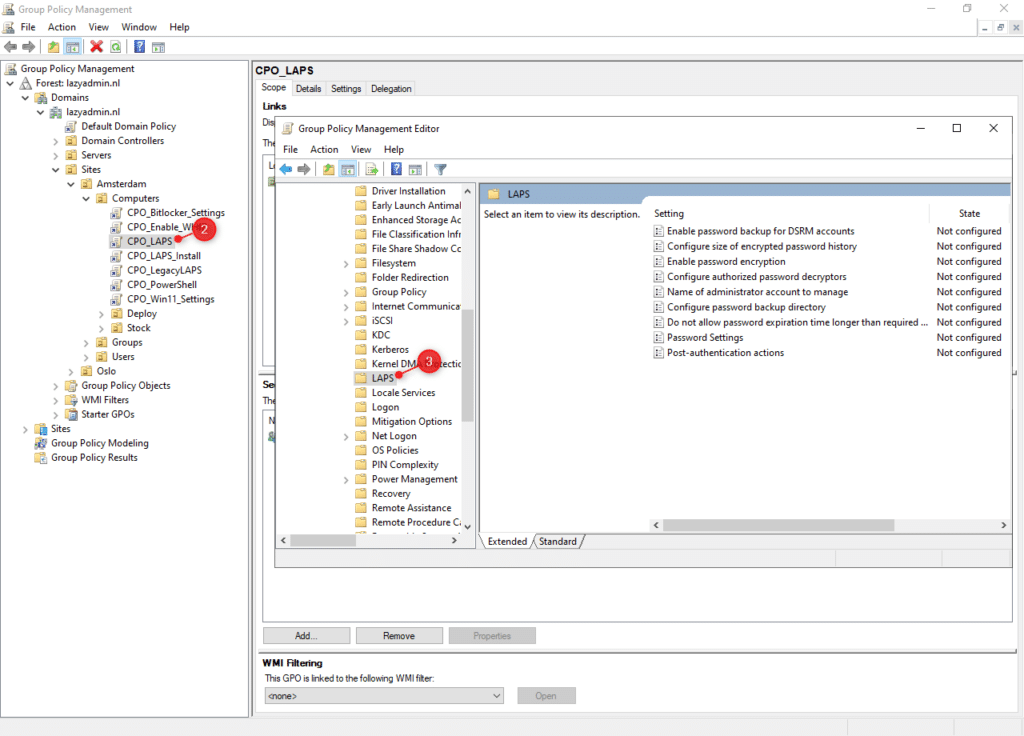
Observe
Should you don’t see LAPS below Administrative Templates > System then copy the ADMX recordsdata from C:WindowsPolicyDefinitions to your central retailer :contoso.comSYSVOLcontoso.compoliciesPolicyDefinitions
- Open Configure password backup listing and set it to both Lively Listing or Azure Lively Listing. Make it possible for your machine is managed within the AD that you choose.

- Open Password Settings and allow the setting. Optionally change the configuration.
- (Non-obligatory) Open Identify of administrator account to handle, allow it, and set the account identify to LAPSAdmin. Should you don’t configure this setting, then the built-in Administrator account shall be used.
There are a few different settings that you simply may wish to allow. I like to recommend enabling a minimum of the setting Publish-Authentication actions. This setting is triggered when the LAPS password is used. It’ll reset the password and optionally logoff the managed account after for instance 8 hours:
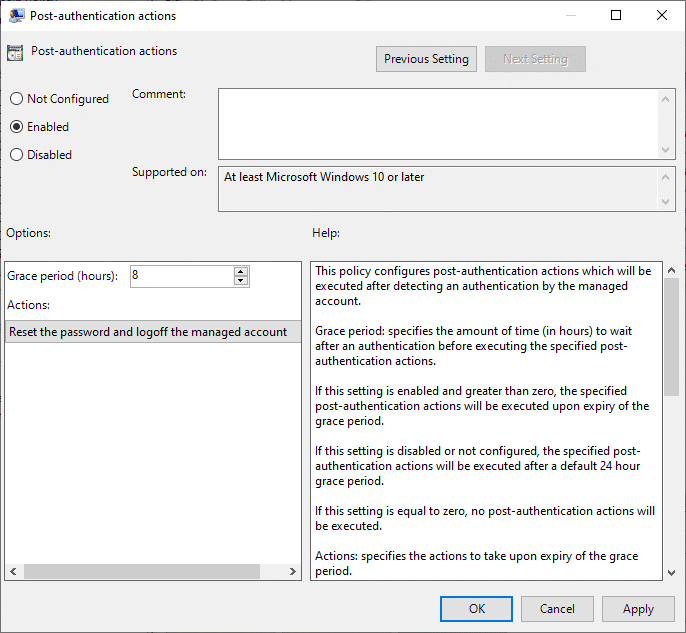
Should you create snapshots out of your computer systems then it could be attention-grabbing to allow the password historical past setting. This can retailer the final 12 passwords within the AD, permitting you to log in with the native admin account when restoring an outdated snapshot. To make use of this setting you’ll need to allow password encryption as nicely.
Step 5 – Create a neighborhood admin account
The brand new Home windows LAPS characteristic doesn’t create a neighborhood admin account mechanically identical to the legacy LAPS did. The simplest possibility is to make use of the built-in Administrator account and don’t configure a singular admin account for laps.
However if you happen to nonetheless wish to use a devoted account, then you’ll need to create a brand new native admin account with PowerShell for instance. We are able to add the next PowerShell script to the start-up scripts within the Group Coverage (Pc Configuration > Home windows Settings > Scripts > Startup)
If ($null -eq (Get-LocalUser -Identify "lapsadmin")) Add-LocalGroupMember -Group directors
Step 6 – Confirm Settings
To confirm the settings we’ll want a Home windows 10 or 11 machine with the newest updates put in. We first want to tug the newest coverage settings to the machine, in order that the LAPS password is created and written again to the Lively Listing. You possibly can both run the GPUpdate command or the particular LAPS Coverage cmdlet Invoke-LapsPolicyProcessing:
Invoke-LapsPolicyProcessing
After the coverage is retrieved, we will confirm the LAPS password within the Lively Listing. Search for the machine and open the properties. Should you open the LAPS tab you will note the LAPS password:
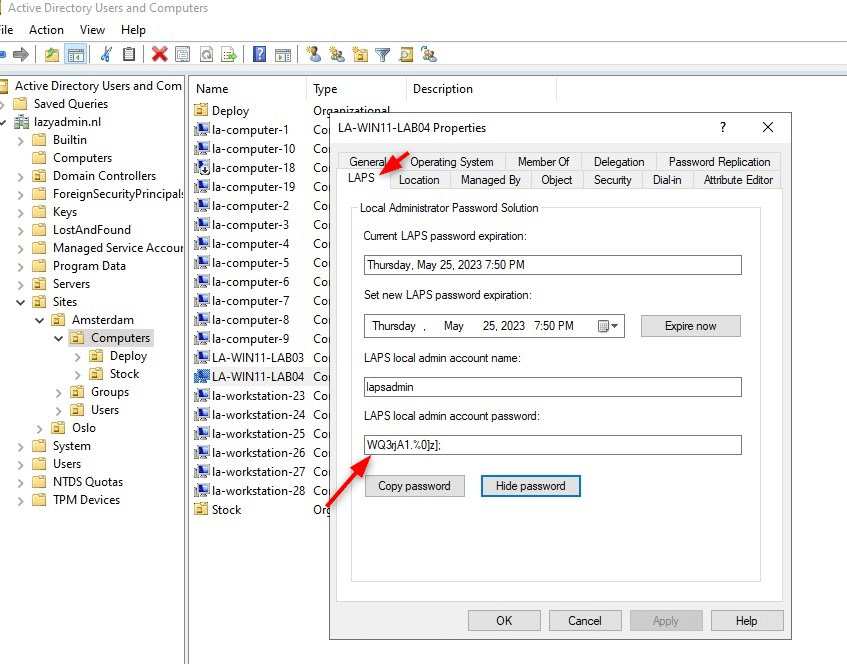
Handle LAPS with PowerShell
The Home windows LAPS PowerShell module is now included into Home windows. Because of this we don’t must import a brand new module to handle LAPS with PowerShell. I received’t undergo all cmdlets (you will discover the whole checklist right here), however we’ll talk about an important ones.
We are able to use the cmdlet Get-LapsADPassword to view the LAPS password. Just be sure you add the parameter -AsPlainText to truly view the password.
Get-LapsADPassword -Id la-win11-lab04 -AsPlainText ComputerName : LA-WIN11-LAB04 DistinguishedName : CN=LA-WIN11-LAB04,OU=Computer systems,OU=Amsterdam,OU=Websites,DC=lazyadmin,DC=nl Account : lapsadmin Password : WQ3rjA1.%0]z]; PasswordUpdateTime : 4/25/2023 7:50:36 PM ExpirationTimestamp : 5/25/2023 7:50:36 PM Supply : EncryptedPassword DecryptionStatus : Success AuthorizedDecryptor : LAZYADMINDomain Admins
Now I like to recommend to configure the coverage to mechanically reset the password after it’s used. However we will additionally reset (rotate) the password with PowerShell. This cmdlet must be run on the endpoint, or you’ll need to run the command remotely with Invoke-Command
Reset-LapsPassword
# Run it on a distant pc
Invoke-Command -ComputerName LA-Win11-Lab04 -ScriptBlock {Reset-LapsPassword}
Deploy LAPS with Intune
In case your gadgets are managed by way of Intune then you can too deploy Home windows LAPS with Intune. We don’t want to put in something, we solely must create a brand new coverage for our endpoints in Intune. Earlier than we begin we might want to guarantee that LAPS is enabled in Azure AD:
- Open portal.azure.com
- Click on on the Azure Lively Listing
- Open Gadgets > Machine Settings
- Allow Azure AD Native Administrator Password Resolution (LAPS)
- Click on on Save
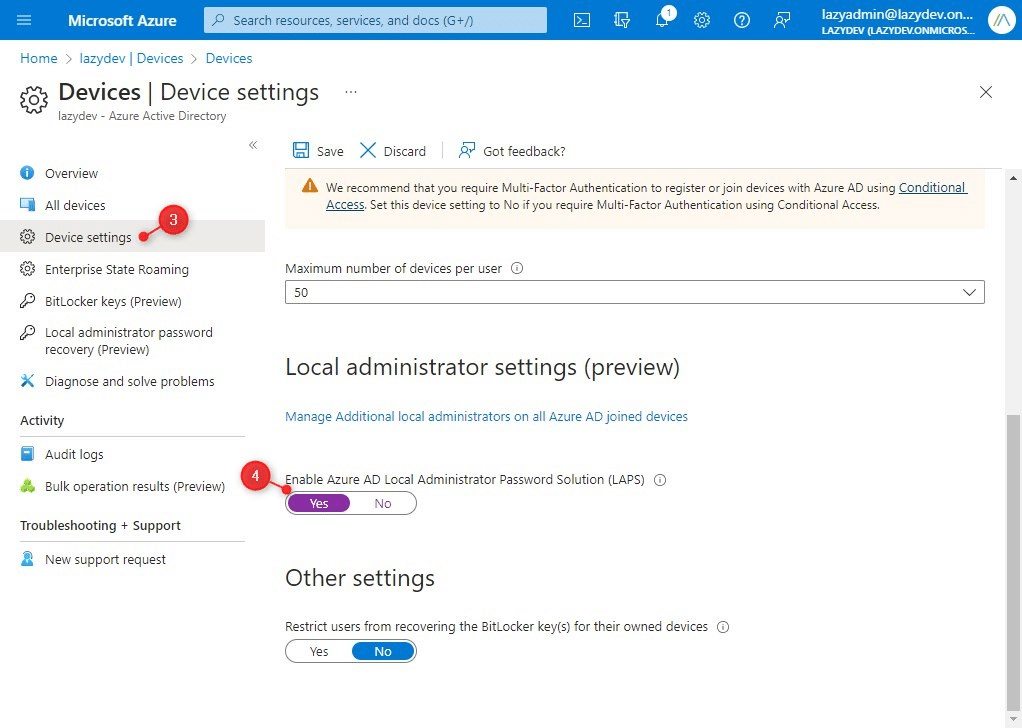
With LAPS enabled in Azure AD, we will now create the brand new coverage:
- Open Endpoint Supervisor (Intune)
- Go to Endpoint Safety > Account Safety
- Create a new coverage
- Choose the platform Home windows 10 and later and the profile Native admin password answer
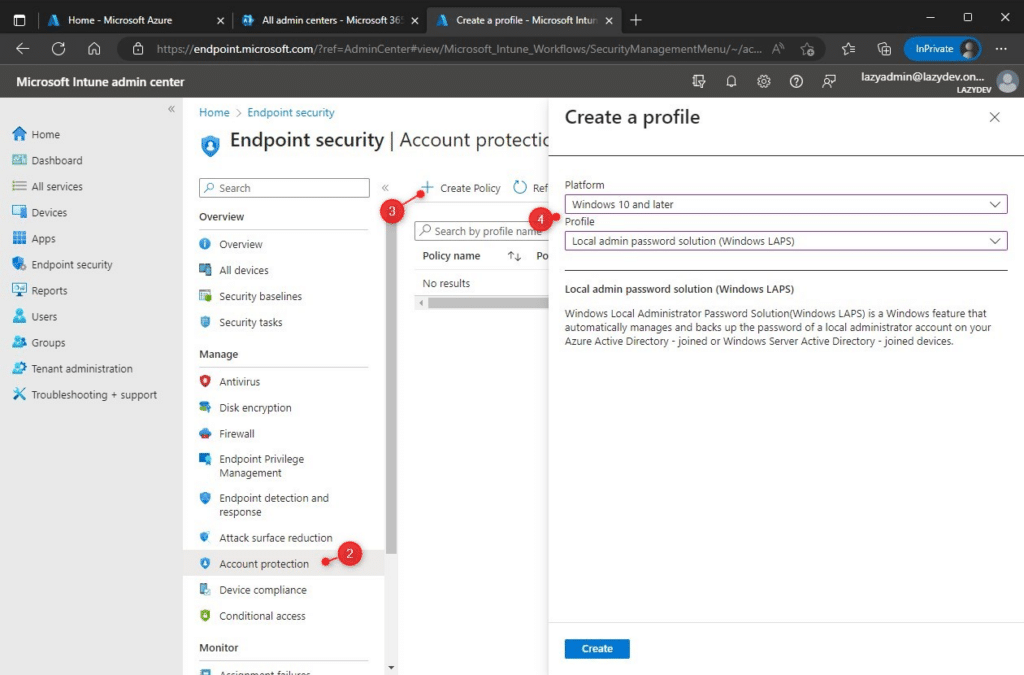
- Give the profile a reputation, for instance, Home windows LAPS
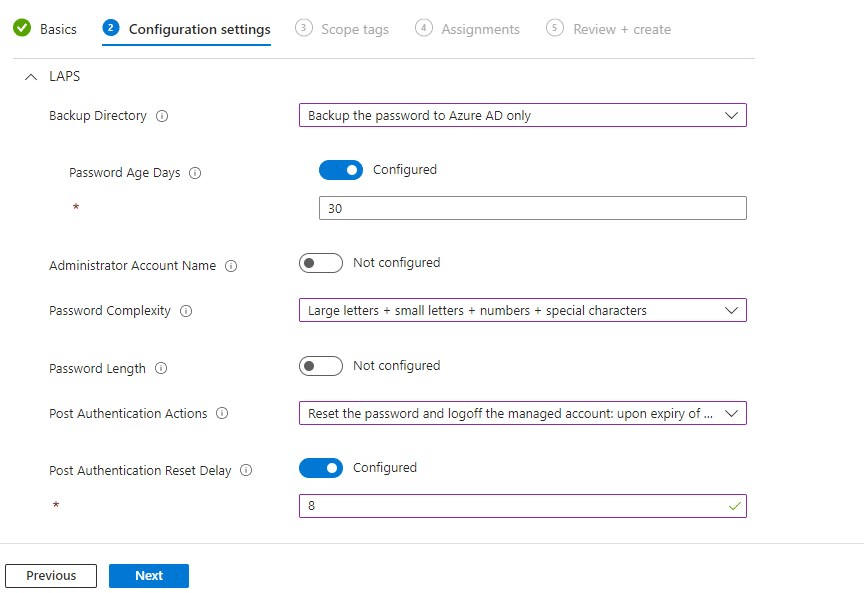
- In step 2 we might want to configure the next settings a minimum of:
- Backup Listing > Backup the password to Azure AD solely
- Password Age Days > 30
- Password Complexity > Select one of many choices
- Password Size > Default is 14, you possibly can change it. Minimal is 8
- Publish Authentication Actions > Set to Reset password and log out the managed account.
- Reset Delay > 8 hours
- You possibly can skip the Scope tags
- Assignments > Add a bunch with gadgets on which you wish to deploy Home windows LAPS
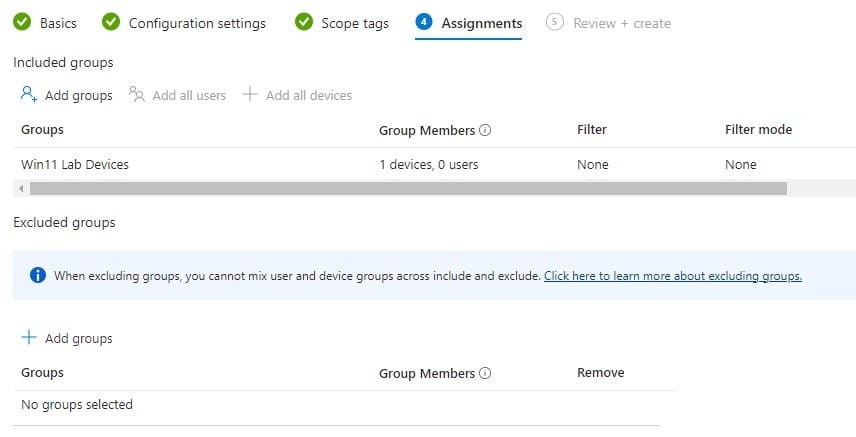
- Evaluation the settings and create the brand new coverage
After you could have created and assigned the coverage it could possibly take a while earlier than it’s deployed to all of the endpoints. You possibly can power the synchronization of the coverage within the Intune Admin heart by opening a tool and clicking on sync.
To view the progress of the rollout, you’ll need to return to Endpoint Safety > Account Safety, open the newly created coverage, and click on on View Report.
Viewing the LAPS Password
We’ve a few choices to view the LAPS password of gadgets. Essentially the most handy approach is to open both Azure AD or Intune (Endpoint Supervisor). An alternative choice is to make use of PowerShell with Microsoft Graph to retrieve the passwords, however that requires some configuration earlier than you need to use it.
To view the passwords within the Azure AD, open Gadgets and click on on Native Administrator password restoration. This offers you an inventory of all gadgets the place LAPS is energetic and means that you can present the password.
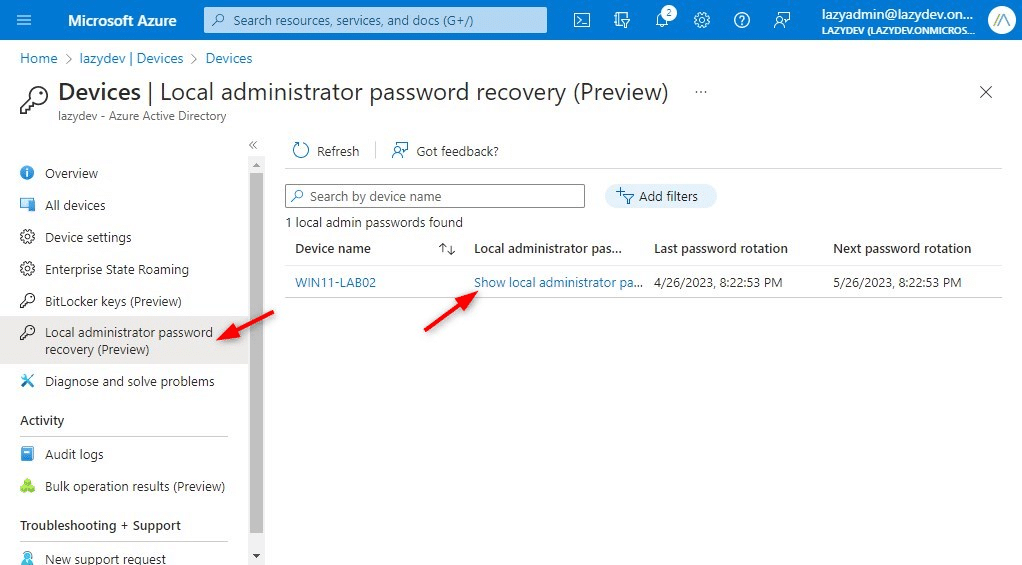
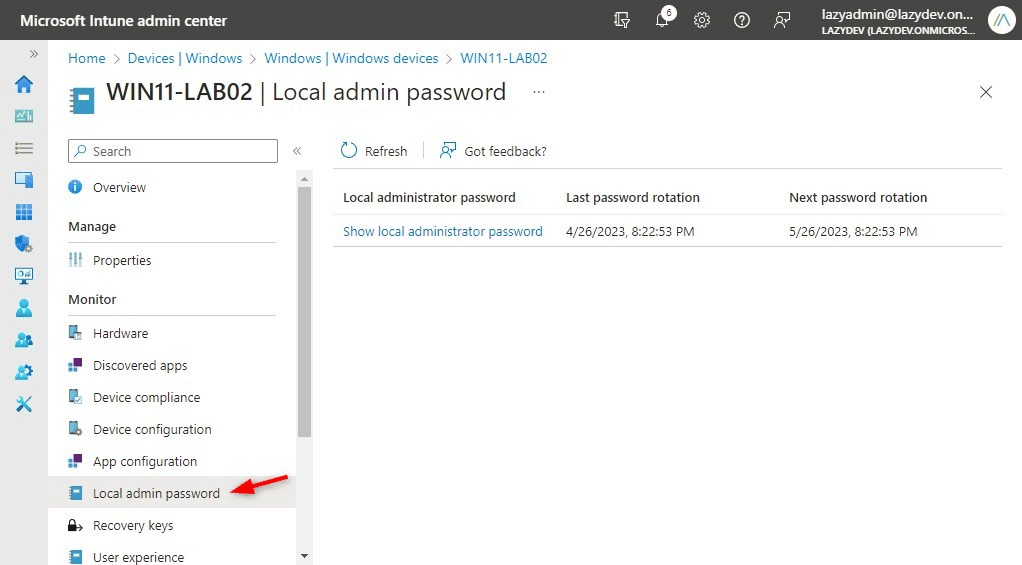
You may as well view the password by first opening the machine in Azure AD. The opposite possibility is to make use of Intune (Endpoint Supervisor). Should you navigate to the machine and open it, you will note Native Admin Password within the sidebar. Click on on it to indicate the native administrator password:
Migrate Microsoft LAPS to Home windows LAPS
When you could have the outdated Microsoft LAPS (legacy LAPS) already working in your atmosphere, then you possibly can simply migrate to the brand new Home windows LAPS. Vital to notice is that we will re-use the LAPS admin account identify, we’re principally going to arrange Microsoft and Home windows LAPS side-by-side. If all the pieces runs nice within the new model, then we will take away the legacy LAPS.
Step 1 – Deploy Home windows LAPS
Set up Home windows LAPS with the steps described above, extending the AD schema, setting permissions, and configuring the coverage. Within the coverage, just be sure you use a singular native admin account identify, for instance, lapsadmin2.
Step 2 – Add the native Admin Account to your Gadgets
We might want to manually create the brand new native admin account on the gadgets. You should use the identical PowerShell script as described earlier:
If ($null -eq (Get-LocalUser -Identify "lapsadmin2")) Add-LocalGroupMember -Group directors
Step 3 – Take a look at the brand new Home windows LAPS
You possibly can run the brand new Home windows LAPS side-by-side with the legacy LAPS to check the brand new answer.
Step 4 – Take away the Legacy LAPS
If the brand new answer is working as anticipated, then we will begin with eradicating the legacy LAPS from the purchasers. Uninstall the Microsoft LAPS consumer from the gadgets, take away the outdated LAPS Admin account and take away the outdated insurance policies.
Troubleshooting LAPS points
Insurance policies are all the time a bit onerous to troubleshoot. For LAPS we acquired a few choices to debug any drawback that comes up. Step one could be to test the occasion viewer. Yow will discover all occasions associated to LAPS within the occasion viewer below Functions and Companies > Microsoft > Home windows > LAPS:
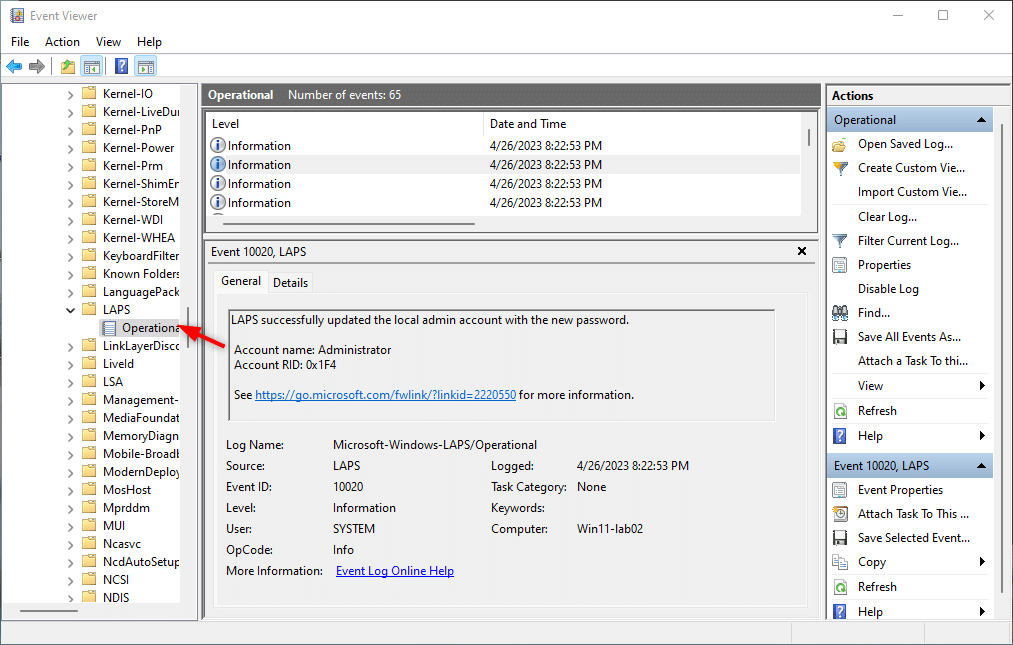
If you’re utilizing Intune for the deployment of Home windows LAPS, then you can too view the report within the Intune Admin Heart (Endpoint Supervisor). Open the coverage in Endpoint Safety > Account Safety and click on on View Report.
An alternative choice is to generate a diagnostics report with PowerShell. Run the cmdlet Get-LapsDiagnostics on the endpoint to generate a report. Within the export, you will see that an occasion log and CSV file will all of the occasions associated to LAPS.
FAQ
To increase the AD Schema, you’ll need to be a member of the Safety Group Schema Admins which you will discover within the Lively Listing. Just be sure you log out / on after you added the account to Schema Admins.
Just be sure you have put in the newest updates in your Home windows servers and restarted the server after updating.
You will have to allow LAPS in your Azure Lively Listing. Within the Azure Lively Listing open Gadgets > Machine Settings and allow Native Administrator Settings. This error can also be listed within the occasion log below occasion id 10059
Wrapping Up
The brand new Home windows LAPS is a good enchancment over the older Microsoft LAPS answer. Every little thing you want is now built-in to the newest Home windows construct, making it a strong answer. The implementation of the brand new model is fairly simple, particularly if you’re utilizing Microsoft Intune (Endpoint supervisor).
I hope this text helped you with implementing the brand new LAPS. You probably have any questions or ideas, simply drop a remark beneath.


