Written by Harry Roberts on CSS Wizardry.
Desk of Contents
A trivial efficiency optimisation to assist pace up third-party or other-origin
requests is to preconnect them: trace that the browser ought to preemptively open
a full connection (DNS, TCP, TLS) to the origin in query,
for instance:
<hyperlink rel=preconnect href=https://fonts.googleapis.com>
In the precise circumstances, this straightforward, single line of HTML could make pages
lots of of milliseconds
quicker!
However repeatedly, I see builders misconfiguring even this most simple of
options. As a result of, as is commonly the case, there’s rather more to this ‘primary
characteristic’ than meets the attention. Let’s dive in…
Be taught by Instance
On the time of writing, the BBC Information homepage (in
the UK, at the very least) has these 4 preconnects outlined early within the <head>:
<hyperlink rel=preconnect href=//static.bbc.co.uk crossorigin>
<hyperlink rel=preconnect href=//m.recordsdata.bbci.co.uk crossorigin>
<hyperlink rel=preconnect href=//nav.recordsdata.bbci.co.uk crossorigin>
<hyperlink rel=preconnect href=//ichef.bbci.co.uk crossorigin>
Readers on slim screens ought to know that every of those preconnects
additionally carries a crossorigin attribute—scroll alongside to see for your self!
Be aware that the BBC use schemeless URLs (i.e. href=//…). I might not
suggest doing this. At all times pressure HTTPS when it’s out there.
Having consulted for the BBC various instances, I do know that they make heavy use
of inside subdomains to share assets throughout groups. Whereas this fits
developer ergonomics, it’s not nice for efficiency, significantly in circumstances
the place the subdomain in query is on the essential path. Warming up connections
to essential origins is a should for the BBC.
Nonetheless, a take a look at a waterfall tells me that none of those preconnects labored!
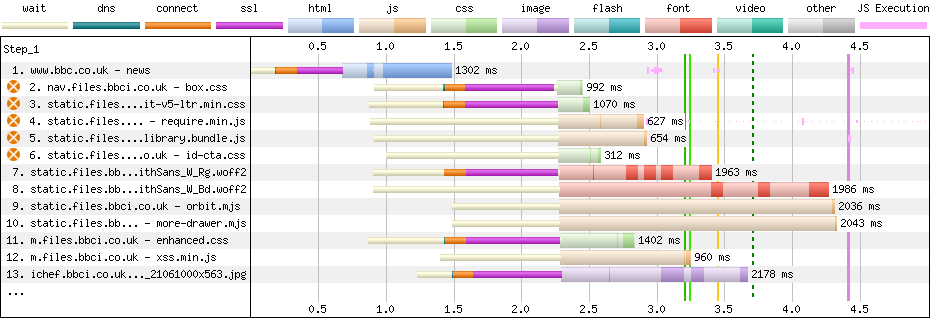
Above, you’ll be able to see that the browser found references to every of those
origins within the first chunk of HTML, earlier than the 1-second mark. That is evidenced
by the sunshine white bars that denote ‘ready’ time—the browser is aware of it wants
the recordsdata, however is ready to dispatch the requests. Nonetheless, we will additionally see
that the browser didn’t start community negotiation till nearer to the 1.5-second
mark, once we start seeing a tiny slither of inexperienced—DNS—adopted by the rather more expensive TCP and TLS. What went fallacious?!
Working Out Which Origins to preconnect
Within the instance above, we’ve 5 connections to the next 4 domains
(extra on that later):
nav.recordsdata.bbci.co.uk: On the essential path with render-blocking CSS.static.recordsdata.bbci.co.uk: On the essential path with
render-blocking CSS and JS.m.recordsdata.bbci.co.uk: On the essential path with render-blocking CSS.- The screenshot above marks the CSS as non-blocking due to the way in which it’s
fetched—it’spreloaded, which is non-blocking, however it’s then
conditionally utilized to the web page utilizingdoc.write()(which is its personal
efficiency fake pas in itself).
- The screenshot above marks the CSS as non-blocking due to the way in which it’s
ichef.bbci.co.uk: Not on the essential path, however does host the
homepage’s LCP ingredient.
N.B. For neatness, I’m omitting the https:// from
written prose, however it’s vital that you just embrace the related scheme in your
href attribute. All code examples are full and proper.
Every of those 4 origins is significant to the web page, so all 4 could be candidates
for preconnect. Nonetheless, the BBC aren’t trying to preconnect
static.recordsdata.bbci.co.uk in any respect; as an alternative, they’re preconnecting
static.bbc.co.uk, which can be used, however isn’t on the essential path. This
feels extra like a easy oversight or a typo than the rest.
As a rule, if the origin is essential to the web page and is used throughout the first
5 seconds of the page-load lifecycle, preconnect it. If the origin will not be
essential, don’t preconnect it; if it can be crucial however is used greater than 5
seconds into the web page load lifecycle, your precedence must be transferring it sooner.
Be aware that essential
may be very subjective. Your analytics isn’t essential;
your chat consumer isn’t essential. Your consent administration platform is essential;
your picture CDN is essential.
One straightforward solution to get an summary of early and essential origins—and the strategy
I take advantage of when advising purchasers—is to make use of WebPageTest. When you’ve run a take a look at, you
can head to a Connection
View
of the waterfall which exhibits a diagram comprising entries per origin, not per
response:

area: that is HTTP2’s
connection coalescence, out there when origins share the identical IP tackle and
certificates.
As straightforward as that—that’s your record of potential origins!
Don’t preconnect Too Many Origins
preconnect must be used sparingly. Connection overhead isn’t big, however too
many preconnects that both a) aren’t essential, or b) don’t get used in any respect,
is certainly wasteful.
Flooding the community with pointless preconnects early within the web page load
lifecycle can steal precious bandwidth that would have been given to extra
essential assets—the overhead of certificates alone can exceed 3KB. Additional,
opening and persisting connections has a CPU overhead on each the consumer and the
server. Lastly, Chrome will shut a connection if it isn’t used throughout the first
10 seconds of being opened, so should you act too quickly, you would possibly find yourself doing it
once more anyway.
With preconnect, you need to try for as few as attainable however as many as
mandatory. In truth, I might think about too many preconnects a code odor, and
you most likely ought to unravel bigger points like self-hosting your static
property and decreasing reliance on third
events on the whole.
When to Use crossorigin
Okay. Now it’s time to be taught why the BBC’s preconnects weren’t working!
That is the third time I’ve seen this downside this month (and we’re solely 9
days in…). It stems from a misunderstanding round when to make use of crossorigin.
I get the impression that builders assume ‘this request goes to a different
origin, so it should want the crossorigin attribute’. However that’s not what the
attribute is for—crossorigin is used to outline the CORS coverage for the
request. crossorigin=nameless (or a naked crossorigin attribute) won’t ever
alternate any consumer credentials (e.g. cookies); crossorigin=use-credentials will
at all times alternate credentials. Except you understand that you just want it, you virtually by no means
want the latter. However when will we use the previous?
If the ensuing request for a file could be CORS-enabled, you would wish
crossorigin on the corresponding preconnect. Sadly, CORS isn’t the
most simple factor on the planet. Thankfully, I’ve a shortcut…
Firstly, determine a file on the origin that you just’re contemplating preconnecting.
For instance, let’s check out the BBC’s field.css. In DevTools (or
WebPageTest if you have already got one out there—you don’t must run one only for
this activity), take a look at the useful resource’s request headers:

There it’s proper there: Sec-Fetch-Mode: no-cors.
The preconnect for nav.recordsdata.bbci.co.uk doesn’t at present (I’ll
come again to that shortly) want a crossorigin attribute:
<hyperlink rel=preconnect href=https://nav.recordsdata.bbci.co.uk>
Let’s take a look at one other request. orbit-v5-ltr.min.css from
static.recordsdata.bbci.co.uk additionally carries a Sec-Fetch-Mode: no-cors request
header, in order that gained’t want crossorigin both:
<hyperlink rel=preconnect href=https://nav.recordsdata.bbci.co.uk>
<hyperlink rel=preconnect href=https://static.recordsdata.bbci.co.uk>
Let’s maintain trying.
How concerning the font BBCReithSans_W_Rg.woff2 additionally from
static.recordsdata.bbci.co.uk?

Hmm. This does want crossorigin because it’s marked Sec-Fetch-Mode: cors. What
will we do right here?
Easy!
<hyperlink rel=preconnect href=https://nav.recordsdata.bbci.co.uk>
<hyperlink rel=preconnect href=https://static.recordsdata.bbci.co.uk>
<hyperlink rel=preconnect href=https://static.recordsdata.bbci.co.uk crossorigin>
We simply add a second preconnect to open a further CORS-enabled connection
to static.recordsdata.bbci.co.uk. (Keep in mind earlier when the browser had opened 5
connections to 4 origins? One among them was CORS-enabled!)
Let’s maintain going and see the place we find yourself…
Because it stands, the very particular instance of the homepage proper now, wants the
following preconnects. Discover that each one origins didn’t want crossorigin,
besides static.recordsdata.bbci.co.uk which wanted each:
<hyperlink rel=preconnect href=https://nav.recordsdata.bbci.co.uk>
<hyperlink rel=preconnect href=https://static.recordsdata.bbci.co.uk>
<hyperlink rel=preconnect href=https://static.recordsdata.bbci.co.uk crossorigin>
<hyperlink rel=preconnect href=https://m.recordsdata.bbci.co.uk>
<hyperlink rel=preconnect href=https://ichef.bbci.co.uk>
This feels snug! The browser naturally opened 5 connections, so I’m
comfortable to see that we’ve additionally landed on 5 preconnects; nothing is
unaccounted for.
I’d suggest familiarising your self with the complete suite of Sec-*
headers—they’re extremely helpful debugging instruments.
preconnect and DNS
As a result of DNS is just IP decision, it’s
unaffected by something CORS-related. Which means:
- You probably have mistakenly configured your
preconnects to make use of or omit
crossoriginwhen you need to have really omitted or usedcrossorigin,
the DNS step can nonetheless be reused—solely the
TCP and TLS want
discarding and doing once more. That mentioned, DNS is
often—by far—the quickest a part of the method anyway, so rushing it up
whereas lacking out on TCP and
TLS isn’t a lot of an optimisation to have a good time. - You probably have every little thing configured accurately, otherwise you aren’t utilizing
preconnectin any respect, you’ll really see the browser reusing the
DNS decision for a subsequent request that
wants a special CORS mode. If you happen to zoom proper in on this abridged waterfall,
you’ll see that the second CORS-enabled request tostatic.recordsdata.bbci.co.uk
doesn’t incur any DNS in any respect:


