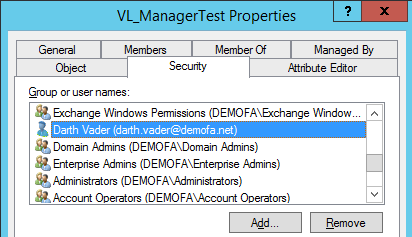
The administration of AD teams doesn’t need to be in IT arms. The ‘Group-Supervisor’ perform is usually used when a non-IT worker within the firm has to handle a gaggle. For instance, the division supervisor ought to be capable of resolve which worker is included in a sure distribution record (i.e. a distribution group).
Supervisor can replace membership record
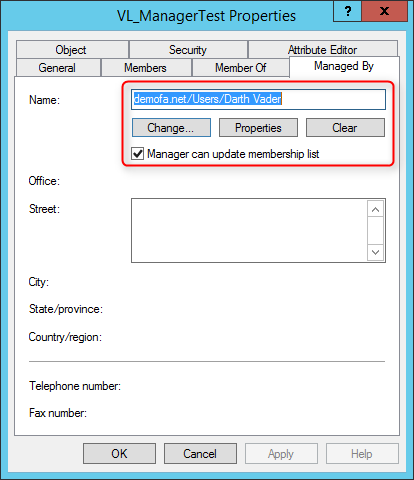
For this goal, the person might be entered within the Energetic Listing Customers and Computer systems console because the supervisor of the group. We are able to additionally test the field: “Supervisor can replace membership record”. The person can then add and take away members, however can’t edit the group.
To this point, so clear. However how does it work if you wish to set this permission by way of PowerShell? This is a little more difficult.
Group-Supervisor Authorization with PowerShell
Choosing the “Supervisor can replace membership record” checkbox doesn’t merely imply setting an attribute on the group. Quite, it adjustments the ACL (Entry Management Listing) of the group. This may also be seen within the safety tab of the group. In precept, this is identical as with permissions on folders.
Let’s assume that our group is named “VL_ManagerTest”. The person who ought to turn out to be supervisor and get permissions to vary members is known as “darkish.vader”. In our Powershell script, we proceed as follows.
Designate customers as managers
First, we set this person as a supervisor. For this we now have to fill the “managedBy” attribute of the group. Nonetheless, this should comprise the distinguishedName of the person. Due to this fact we now have to search out out the distinguishedName and set it. You want this script:
|
$person = Get-ADUser darth.vader Set-ADGroup „VL_ManagerTest“ -Change @{managedBy=$person.DistinguishedName} |
Now the supervisor is about, he nonetheless wants authorizations.
Creating an AccessRule
We have to add an AccessRule for this person to the ACL of the group. To create an ActiveDirectoryAccessRule we’d like 4 info:
- The schema object for which this AccessRule applies.
- The SID of the person to whom the rule applies
- The kind of rule (permit/deny)
- The rights which are to be set
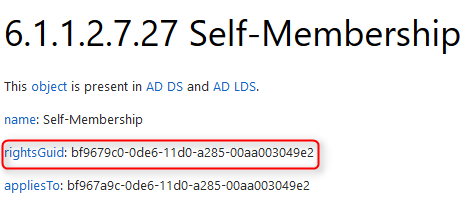
The schema object we’d like right here is “Self-Membership”.
Self-Membership
This object has a “rightsGuid” which we’d like for our ActiveDirectoryAccessRule. The GUID is identical throughout all ADs and might be discovered within the ADSI edit underneath
Configuration -> Prolonged Rights -> Self-Membership -> Properties -> rightsGuid
Nonetheless, a fast Google search results in the identical outcome:
So the very first thing we do is retailer this GUID in a variable.
|
$guid = [guid]‘bf9679c0-0de6-11d0-a285-00aa003049e2’ |
SID of the person
The following info we’d like is the SID of the person. Since we already learn this out earlier, we simply have to convert the kind from String to SecurityIdentifier.
|
$sid = [System.Security.Principal.SecurityIdentifier]$person.sid |
We’d like two extra info; the kind of entry and the permissions we wish to set.
Entry rights of the person
The kind of entry is evident: sure permissions ought to be allowed. The permissions which are wanted listed here are “Write” and “Prolonged Rights“. And that is the way it seems in PowerShell:
|
$ctrlType = [System.Security.AccessControl.AccessControlType]::Enable $rights = [System.DirectoryServices.ActiveDirectoryRights]::WriteProperty -bor [System.DirectoryServices.ActiveDirectoryRights]::ExtendedRight |
Now that we now have all the data we’d like, we will create the rule:
|
$rule = New-Object System.DirectoryServices.ActiveDirectoryAccessRule($sid, $rights, $ctrlType, $guid) |
Creating an ActiveDirectoryAccessRule
Within the final step, we now want so as to add our newly created rule to the ACL of the group. To do that, we should first learn the prevailing ACL:
|
$group = Get-ADGroup „VL_ManagerTest“ $aclPath = “AD:” + $group.distinguishedName $acl = Get-Acl $aclPath |
To this ACL we add our newly created rule after which overwrite the group’s ACL with our modified ACL:
|
$acl.AddAccessRule($rule) Set-Acl -acl $acl -path $aclPath |
With this we now have it achieved. After updating, within the properties of the group underneath “managedBy” ought to be
- the brand new person stand and
- the checkbox “Supervisor can replace membership record” should be set.
Automate group administration
Much less work for everybody and excessive safe stage assure. For this we use the software DynamicGroup. Due to highly effective filters, you may set Attribute necessities for the members of your teams. For instance: A bunch “solely settle for energetic members”. If the standing of a member change to “inactive”, the member will probably be eliminated of the group. For those who replace the division attribute of a person to “gross sales”, DynamicGroup will add this person to all of the teams with this requirement. You possibly can learn extra particulars about this function on this article: Automated permissions based mostly on properties.
You possibly can obtain and check DynamicGroup totally free throughout 30-days right here.
The entire script: Set Group Supervisor Permission with PowerShell
Lastly, right here is the whole script:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
#Supervisor setzen $person = Get-ADUser darth.vader Set-ADGroup „VL_ManagerTest“ -Change @{managedBy=$person.DistinguishedName} #RightsGuid $guid = [guid]‘bf9679c0-0de6-11d0-a285-00aa003049e2’ #SID des Managers $sid = [System.Security.Principal.SecurityIdentifier]$person.sid #ActiveDirectoryAccessRule erstellen $ctrlType = [System.Security.AccessControl.AccessControlType]::Enable $rights = [System.DirectoryServices.ActiveDirectoryRights]::WriteProperty -bor [System.DirectoryServices.ActiveDirectoryRights]::ExtendedRight $rule = New-Object System.DirectoryServices.ActiveDirectoryAccessRule($sid, $rights, $ctrlType, $guid) #Gruppen-ACL auslesen, neue Regel hinzufügen und ACL der Gruppe überschreiben $group = Get-ADGroup „VL_ManagerTest“ $aclPath = “AD:” + $group.distinguishedName $acl = Get-Acl $aclPath $acl.AddAccessRule($rule) Set-Acl -acl $acl -path $aclPath |
Extra query about PowerShell oder Energetic Listing Automation? Assist wanted?
Did this aid you? Share it or depart a remark:
Article created: 01.03.2021