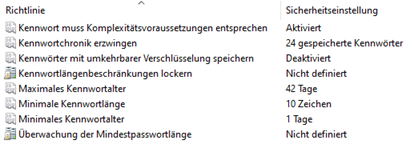
On this article you’ll discover ways to keep away from strings in passwords with Azure AD password safety. By default, the Home windows working system, through the password insurance policies, gives to specify the minimal variety of characters, in addition to a predefined complexity of the password.
This outlined complexity (if enabled) requires:
- {that a} new password should comprise a minimum of one character from three outlined units (uppercase letters, lowercase letters, numbers and particular characters),
- and that the content material of the Energetic Listing attribute sAMAccountName and substrings of the attribute displayName (separated by comma, interval, hyphen, underscore, house, hash or tab) result in rejection.
For necessities going past this for the exclusion of strings, a separate password filter should be created and included.
Keep away from strings in passwords with Azure AD password safety
Within the Microsoft cloud, the Azure Energetic Listing (Azure AD) password coverage doesn’t supply any vital variations for strings, in opposite to Energetic Listing On-premise.
However there may be an extra performance referred to as Azure AD Password Safety, whose keep away from “weak” passwords. Azure AD Password Safety relies on two lists:
- International Blacklist: This listing is managed by Microsoft and up to date through Azure AD telemetry knowledge, with world password leaks or extra weak strings. That is an ongoing course of to fulfill present circumstances.
- Customized Blacklist: This listing is managed below one’s personal duty. One can exclude that e.g. the corporate title or product title could also be utilized in passwords.
With the offered strings, the entered string is evaluated with some extent system in case of a password change. If the worth is a minimum of 5, the string is taken into account legitimate. The method of scoring is as follows:
- Normalization: on this step, uppercase letters are changed by their lowercase counterpart and customary character substitutions (e.g., “0” to “o”, “$” to “s”, or “1” to “l”) are reversed (instance: “P@$$w0rd” turns into “password”).
- Fuzzy match: the entries from the blacklists are searched utterly or as a partial match within the normalized string. An edit distance of 1 can also be utilized, i.e. the entry from the blacklists differs with the (partial) string by an insert, delete or substitute operation. (Instance: “password” = “password” or “password” = “passort”).
- Predefined strings: The respective strings higher than three characters consisting of first title, final title, and Azure shopper title will end in direct password rejection if a match is discovered
- Scoring: Every fuzzy match discovered is scored with one level. All remaining characters are moreover calculated with one level.
The worldwide Blacklist is accessible by default for every cloud-based consumer account. To make use of a customized blacklist, a minimum of one Azure AD Premium P1 license is required.
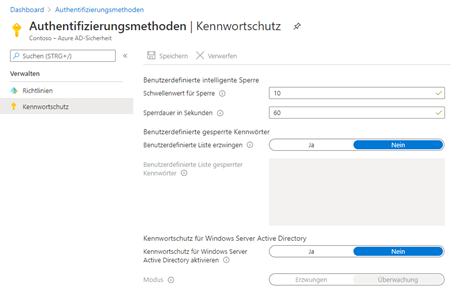
Cloud password safety for native consumer accounts
Microsoft has prolonged the performance to incorporate a element for the Home windows Server Energetic Listing. It signifies that the worldwide and, if used, the personalised blacklist can be utilized when a password change is made to an Energetic Listing consumer account with the ranking system described above. The performance may be operated in one in every of two modes:
- Monitoring mode: on this mode, a password change is allowed in response to the domestically relevant password coverage, however compliance or rejection in opposition to the backlists is famous within the occasion log of the respective area controller.
- Enforcement mode: On this mode, the native password coverage and the Azure AD password safety apply when a password change happens. As well as, as within the monitoring mode, corresponding info is famous within the occasion log.
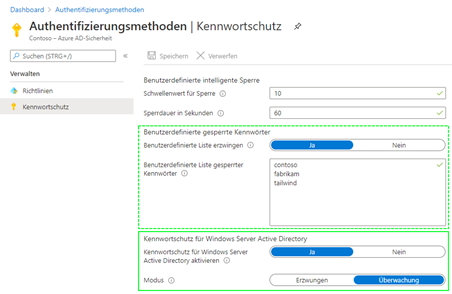
Independently, the blacklist lists are cached within the SYSVOL share. Each hour, every area controller verifies the age of the blacklists. If they’re older than one hour, an replace is requested.
Azure AD Password Safety with Home windows Server Energetic Listing
Microsoft has arrange an structure diagram for this performance so that straightforward deployment with out planning may be dominated out. However first, let’s have a look at the conditions:
- An Azure tenant
- All Azure consumer accounts which can be synchronised from Home windows Server Energetic Listing into Azure AD will need to have a minimum of one Azure AD Premium P1 licence assigned (all non-synchronised customers can also use Azure AD password safety).
- At the least one member server that performs proxy performance between the brokers on the area controllers and the Azure AD (should not embrace the Azure AD utility proxy).
- Replication of the SYSVOL folder construction within the Home windows Server Energetic Listing is carried out utilizing the DFS-R service (the file replication service is just not supported).
If these conditions are fulfilled, the required companies may be arrange and the performance for the Home windows Server Energetic Listing may be activated. For this function, please consult with the structure diagram already talked about:
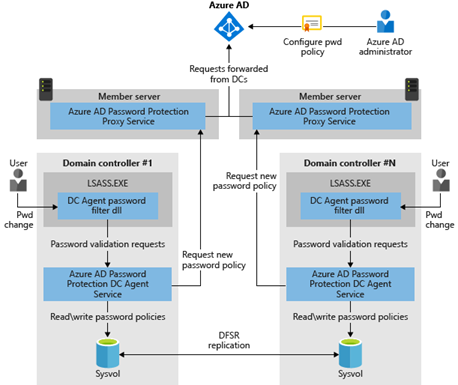
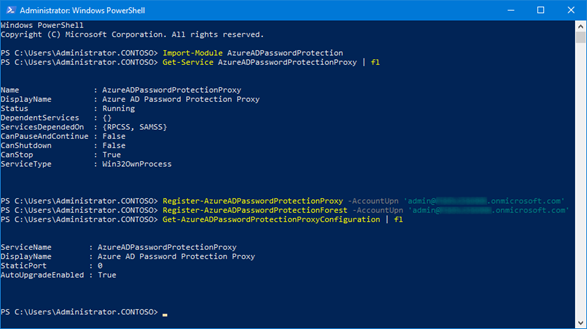
The setup begins with the Azure AD password safety proxy service, which is put in on a member server within the Energetic Listing forest to be deployed (e.g. on the Azure AD Join system). For higher failover safety of the service, it ought to be scheduled on one other system. A Service Connection Level (SCP) is created within the Home windows Server Energetic Listing for every occasion of the proxy service through PowerShell cmdlet and the registration in Azure AD is carried out on the similar time (Azure AD International Admin and Organisation Admin are required for this).
If a number of Home windows Server Energetic Listing forest constructions within the company community are to make use of Azure AD password safety, then a minimum of one occasion of the Azure AD password safety proxy service is required for every forest. As well as, every Home windows Server Energetic Listing forest should be made recognized as soon as for Azure AD password safety in Azure AD.
After the proxy service is deployed within the on-premises infrastructure, the Azure AD Password Safety DC brokers may be put in on area controllers. Throughout set up, an extra password filter DLL is registered on the area controller, which communicates with the Azure AD Password Safety DC Agent to confirm a password in opposition to the native copies of the 2 blacklists.
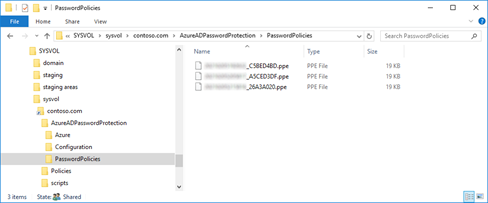
The password filter DLL is an addition to the already present filters. For the Energetic Listing, a string is legitimate if all password filters comply with it. To acquire an replace of the blacklists, the Azure AD Password Safety DC Agent communicates with the proxy service discovered through the registered SCP within the Energetic Listing. A newly acquired listing is saved within the SYSVOL file construction (see image) and thus replicated to all area controllers of the area, in order that not each area controller has to request the blacklists both.
The deployment of the brokers to all area controllers of a website may be completed in phases, in order that on this case the Azure AD password safety is just energetic on the area controllers on which the Azure AD password safety DC agent can also be in operation. I.e. if a consumer adjustments his password on a website controller on which the agent is just not but deployed, then the 2 predefined blacklists don’t apply. This process can be utilized, for instance, for preliminary checks of the performance within the productive infrastructure.
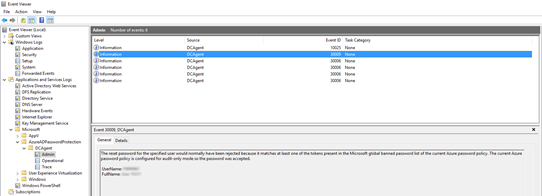
The Azure AD password safety ought to first be utilized in monitoring mode in an effort to familiarise oneself as an administrator with the operation of the service. If essential, the results of the 2 blacklists may be assessed or customers may be alerted to an unfavorable composition of the chosen strings in their very own password. In a second step, the mode can then be modified and the Azure AD password safety absolutely activated.
Conclusion
If the required Azure licences can be found, then the standard of the consumer passwords in Azure AD and within the Home windows Server Energetic Listing of an organization may be elevated with comparatively easy means. The net interface within the Azure Portal gives the likelihood to take care of the user-defined blacklist for Azure AD and Home windows Server Energetic Listing uniformly. On the company community, the structure of the service prevents area controllers from sustaining a direct communication path with a cloud service. An area cache compensates for a short lived limitation within the accessibility of the cloud service.
For a consumer, the setup of strings in passwords is clear. Whether or not through a password coverage or Azure AD password safety, the consumer receives the equivalent cryptic indication that his or her chosen string violates a password requirement. An administrator, except he has a centralised assortment service for occasions, should discover the corresponding area controller on which the password change was made. He should then seek for the log entry that gives info on why a string was rejected based mostly on Azure AD password safety.
Extra query about PowerShell oder Energetic Listing Automation? Assist wanted?
Did this provide help to? Share it or go away a remark:
Article created: 10.05.2021



