If you’re concerned in assist or improvement, typically you could use secrets and techniques, passwords, or
subscription keys in PowerShell scripts. These must be saved safe and separate out of your scripts
however you additionally want entry to them ALL THE TIME.
So as an alternative of hand getting into them each time they need to be saved in a key retailer of some kind that
you may entry programmatically. Typically off the shelf keystores are usually not out there in your setting
or are clumsy to entry with PowerShell. A easy method to have quick access to those secrets and techniques with
PowerShell can be useful.
You can merely have them in plain textual content, in your machine solely, making it comparatively safe.
Nevertheless, there are lots of dangers with this method, so including some extra safety is a superb
concept.
The .NET lessons sitting behind PowerShell present some easy methods to do that. This weblog will go
by way of
- Fundamental encryption / decryption
- Utilizing it day-to-day
- Your personal form-based key retailer
Fundamental encryption / decryption
The defend and unprotect strategies out there as a part of the cryptography lessons are
simple to make use of. Nevertheless they use Byte arrays that we will simplify by wrapping their use in a String.
The next examples will be discovered on the MachineAndUserEncryption.ps1 module in my
ps-community-blog repository on GitHub.
Encryption
Perform Defend-WithUserKey {
param(
[Parameter(Mandatory=$true)]
[string]$secret
)
Add-Kind -AssemblyName System.Safety
$bytes = [System.Text.Encoding]::Unicode.GetBytes($secret)
$SecureStr = [Security.Cryptography.ProtectedData]::Defend(
$bytes, # comprises information to encrypt
$null, # optionally available information to extend entropy
[Security.Cryptography.DataProtectionScope]::CurrentUser # scope of the encryption
)
$SecureStrBase64 = [System.Convert]::ToBase64String($SecureStr)
return $SecureStrBase64
}Simply going by way of the strains we will see
- PowerShell must know in regards to the .NET lessons (I’ve examined beneath model 5 & 7 of PowerShell)
- We have to convert our string right into a Byte array
- Use the .NET class to encrypt
- Convert the encrypted Byte array to a string for straightforward storage and retrieval
- Return that string
Decryption
Perform Unprotect-WithUserKey {
param (
[Parameter(Mandatory=$true)]
[string]$enc_secret
)
Add-Kind -AssemblyName System.Safety
$SecureStr = [System.Convert]::FromBase64String($enc_secret)
$bytes = [Security.Cryptography.ProtectedData]::Unprotect(
$SecureStr, # bytes to decrypt
$null, # optionally available entropy information
[Security.Cryptography.DataProtectionScope]::CurrentUser) # scope of the decryption
$secret = [System.Text.Encoding]::Unicode.GetString($bytes)
return $secret
}Steps are similar for the decryption, utilizing barely completely different strategies
- PowerShell must know in regards to the .NET lessons
- We have to convert our string right into a Byte array
- Use the .NET class to decrypt
- Convert the encrypted Byte array to a string
- Return that string
Utilizing it day-to-day
That is actually helpful if you’re doing repetitive duties that want these values. Typically in a assist
position, investigations utilizing API’s can velocity up the method of study, and likewise give you a
fast method to do fixes that don’t require heavy use of a GUI primarily based setting.
Assigning a key to a secret worth, and storing that in a hash desk format is the only method to
have entry to those values AND hold them saved domestically with a level of safety. Your code can
then dynamically lookup these values, and if different assist folks retailer the identical key domestically the
identical method (typically with completely different values, consider an API password and or username pair) then your
script can work for everybody.
Once more, MachineAndUserEncryption.ps1 in my repository on my GitHub has features for persisting and
utilizing this data. For compatibility with model 5 & 7 you additionally want the operate
ConvertToHashtableV5.
I’d additionally advocate utilizing Defend-WithMachineAndUserKey and Unprotect-WithMachineAndUserKey
when implementing domestically, they add one other layer of safety.
Your personal form-based key retailer
When you have adopted my different 2 blogs a few scalable setting and
easy kind improvement then utilizing the sources from these we will simply create our personal kind
to handle our secrets and techniques. In reality, if in case you have downloaded and put in the modules for both of these
blogs (they’re the identical, and this weblog references the identical as effectively), you’ve gotten it able to go.
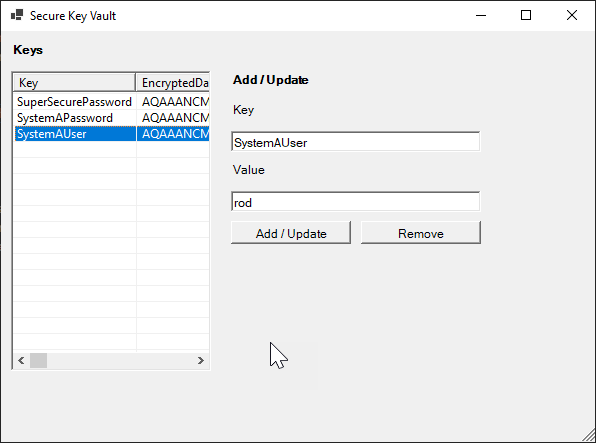
Upon getting your setting arrange, merely run the cmdlet:
New-EncryptKeyFormand if all is about up appropriately, it’s best to see
Conclusion
Balancing the pragmatic ease of use and safety issues round secrets and techniques you could want to make use of all day
daily could be a wonderful balancing act. Utilizing some easy strategies, we will strike that stability and
hopefully be securely productive.
Lets safe some stuff!


