Written by Harry Roberts on CSS Wizardry.
Desk of Contents
A big a part of my efficiency consultancy work is auditing and subsequently
governing third-party scripts, dependencies, and their suppliers. Uncovering
these third-parties isn’t all the time so easy, and discussing them with
the inner groups accountable (as a rule, the Advertising Division)
is normally fairly delicate and sometimes uncomfortable: in any case, approaching
a third-party distributors, or your advertising and marketing staff, and telling them that their
whole day job is detrimental to efficiency isn’t going to be well-received.
To be able to assist me have these awkward discussions—and it’s typically my job as
a guide to be the one having them—I lean on quite a lot of instruments to assist make
the subject as goal and easy as attainable. I wish to share them
with you.
Figuring out
The one most great tool I make use of with regards to merely figuring out
third events is Simon Hearne’s indispensable
Request Map. The workflow round this instrument
is fairly easy:
- drop a URL into the Goal URL subject;
- choose a check location (if geographic locale may have an effect on which third events
are referred to as then this characteristic could also be significantly helpful to you) - submit a check;
- and wait.
As soon as that’s accomplished, you’ll be introduced with what my shoppers and I’ve lovingly
dubbed the jellyfish:
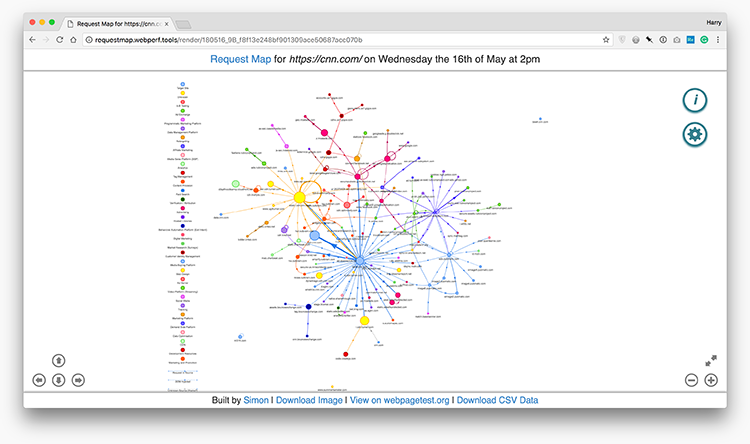
This interactive knowledge visualisation reveals us all the third-party domains that
the URL makes requests to, and their subsequent requests, and so forth.
Every blob (node) represents a site; the dimensions of the node represents the
proportional variety of bytes that area was chargeable for; the gap
between nodes represents the imply TTFB of the area; the thickness of every
line (edge) represents the variety of requests from the area; dotted edges
characterize requests initiated from a script or recognized via a referrer
; round edges characterize requests initiated by the identical area.
header
That takes some time to memorise, so to start out with simply keep in mind that large blobs
imply a lot of bytes, distant blobs imply excessive TTFB, and thick traces imply a lot of
requests. This gives you an at-a-glance thought of the form of issues.
Distinction CNN (above) with CSS Wizardry’s homepage:
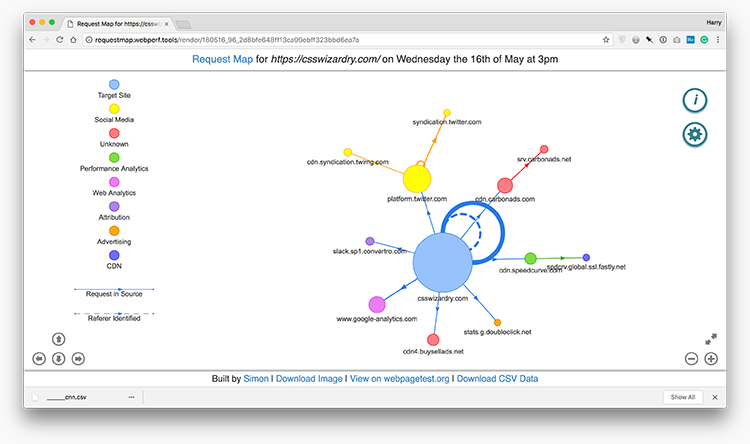
You’ll be able to rapidly see the distinction in third social gathering well being between the 2.
Though there are many different instruments that we will and may use to assist us
audit third events, Request Map is the one I wish to present you proper now.
Auditing
Auditing third events is a large job and might take many alternative types, so I’m
not going to enter an excessive amount of element on this put up: you possibly can all the time rent
me to indicate you every little thing I find out about that.
One instant factor we will do with the information from Request Map is solely get
a broad overview of our worst offenders: whose blobs are the most important? Is anybody
struggling excessive TTFB? Are there any lengthy chains of third, fourth, fifth social gathering
requests?
Taking issues a step additional, one factor I all the time do is rerun a WebPageTest with
all the third events lacking. That is fairly excessive and non-scientific, however
it’s good to get a really fast thought simply how a lot overhead the third events
introduce. To be able to do that, you’ll must obtain the CSV file that
Request Map makes out there to you. There’s a hyperlink proper on the backside of the
Request Map viewport, and that gives you a file that appears just a little like
this:
host, firm, class, total_bytes, average_ttfb, average_load, number_requests
cnn.com, Goal Website, Goal Website, 0, 33, 130, 1
www.cnn.com, Goal Website, Goal Website, 232542, 510, 1473, 11
www.i.cdn.cnn.com, Unknown, Unknown, 617784, 6053, 8335, 20
cdn.optimizely.com, Optimizely, A-B Testing, 120965, 97, 625, 1
cdn.cnn.com, Goal Website, Goal Website, 427640, 6079, 8236, 32
adverts.rubiconproject.com, The Rubicon Undertaking, Advert Change, 25734, 130, 833, 1
js-sec.indexww.com, WPP, Programmatic Advertising Platform, 23605, 177, 873, 1
cdn.krxd.web, Krux Digital, Knowledge Administration Platform, 106664, 266, 1668, 5
static.criteo.web, Criteo, Retargeting, 20938, 44, 833, 1
c.amazon-adsystem.com, Amazon, Affiliate Advertising, 14885, 199, 875, 1
...
Take a look at all that pretty, uncooked knowledge!
N.B. This excerpt has been formatted for presentation.
Subsequent up, when you’re comfy with the command line, let’s run a fast AWK
one-liner to strip out the non-Goal Website entries:
$ awk -F',' '$2 != "Goal Website" { print $1 }' cnn.csv
awkis a comparatively normal text-processing language.-F','tells AWK to make use of a comma as our subject separator (CSVs are, by
definition, comma separated).$2 != "Goal Website"means if the second subject is not Goal Website.{ print $1 }means print out the primary subject, which occurs to be the
area.cnn.csvis the trail to the CSV file we simply downloaded.
It will, very crudely, offer you an inventory of all the web page’s third
social gathering domains. I might all the time advocate sanity-checking this record for any false
positives, and when you’ve cleaned all of it up, copy it to your clipboard.
Now we wish to head again over to WebPageTest and run a check with all of these
domains blocked: let’s see how the web page feels with all of its third events
lacking.
In WebPageTest’s Superior Settings panel, find the Block tab; now paste in
your record of third social gathering domains:
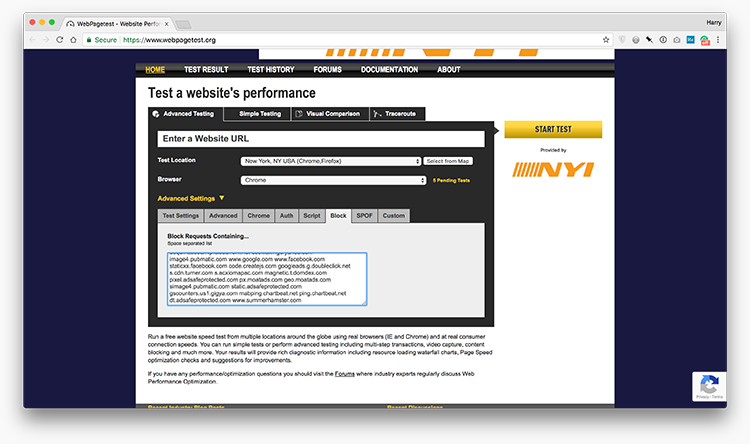
Rerunning the check (with all earlier settings similar the place attainable)
with this record of domains blocked gives you a really broad overview of how
quick the web page could be with all third social gathering assets absent.
This could now arm us with tough knowledge round which we will being centring our
discussions, for instance:
- With all third events current, load time will increase by 6.3s.
- Eradicating all third events lowered the variety of requests by 4.2×.
- With none third events, web page weight dropped by 2.7×.
Once more, I’m eager to emphasize that these insights are pretty non-scientific, however at
this level we simply must know roughly the place we stand. This could assist us
start discussions…
Discussing
The subsequent job, and by far the toughest, is discussing these points with folks,
whether or not that’s the third social gathering supplier themselves, or folks inside your
organisation, it’s not going to be significantly simple. Within the latter camp, you’re
very often coping with knowledge, advertising and marketing, and insights groups: lots of the third
events that web sites make use of are possible non-user dealing with, and usually, though
not all the time, exist solely to serve the enterprise (analytics, AB testing,
retargeting, monitoring, and so on.).
The rationale these discussions are normally so tough to have is as a result of
engineers generally tend to apportion blame—Advertising did this
, the
—and also you’ll not often make progress if you look like
tag supervisor does that
blaming somebody. You’ll be able to’t rock as much as your advertising and marketing division and inform them
that every little thing they do day-in, day-out is unhealthy for the positioning. We’d like a way more
ask, don’t inform method.
To facilitate this, I devised a small Google Sheet that consumes your Request
Map knowledge, and presents the data in a way more digestible and goal
format. By pulling the information right into a extra common type—like ’em or detest ’em,
everybody understands a spreadsheet—we’re a lot better geared up to start
discussing these points with individuals who aren’t used to waterfall charts, flame
graphs, and spider diagrams.
The small demo embedded beneath reveals the exported Request Map knowledge for my
homepage:
The columns ought to all be pretty self-explanatory:
- A, B, and C inform us the area in query, the controller of that area,
and how much service it supplies (the place recognized). - D, E, F, and G present numerical knowledge pertaining to related efficiency
measurements. - H is left clean for now. This is a crucial column that we’ll come again
to just a little later.
The primary factor I wish to present, nevertheless, is the totally different colouring of sure
cells. Cells in columns B and C may be yellow; cells in D, E, F, or
G may be various shades of crimson.
- Yellow cells spotlight a reproduction supplier or service kind, for instance,
two analytics packages, or hitting Fb a number of occasions. - Pink highlights relative severity, and is a scale from white to very-dark
crimson. From the zeroth to the ninetieth percentile, we get a gradual darkening from
white to crimson; the ninetieth to one hundredth percentile all share the identical heaviest shade:
these are your worst 10%, and doubtless need specializing in first.
Utilizing these two varieties of data, we will start honing in on potential
redundancy in duplicate suppliers, and/or the impression and overhead that sure
suppliers carry.
Armed with this uncooked knowledge, it’s time to organise a gathering with whoever is
primarily chargeable for your third social gathering implementations. This could possibly be one
distinct division, a cross part of the enterprise, or something in between.
The purpose of this preliminary assembly is to be taught. Keep in mind: ask, don’t inform.
Keep away from the temptation of coming into the assembly all weapons blazing; you is perhaps
armed with knowledge, nevertheless it’s important that you just don’t weaponise it. Start by explaining
that We’ve been doing just a little housekeeping and begun trying on the third
This units the
events we use. I’ve put collectively an inventory of them however I may actually use your
assist understanding what all of them are and what all of them do.
tone that you just want them, and at this level, you do. The purpose of this assembly
isn’t to eradicate all of our third events, neither is it to undermine anybody’s
efforts: the purpose is to get an thought of why these items are used and what their
perceived worth to the enterprise is.
Instance questions embrace:
- Are you able to discuss me via Google Tag Supervisor?
- What does this specific third-party do for us?
- Who’s chargeable for this service?
- Which companies can we use every day?
- Are there any companies in right here that we don’t recognise?
Start populating the Notes column with solutions, probe additional, and keep away from the
temptation to make any choices within the assembly itself.
As soon as you’re feeling you’ve gathered sufficient solutions, it’s time to go away and draw up
a possible motion plan. Are there third events that no one can clarify?
They’re a direct candidate for elimination. Are there duplicate third events
that do nearly similar jobs? Then which one may you decommission? Are there
any third events that load an inordinate quantity of bytes? Are you able to open assist
tickets with the supplier?
Utilizing the Google Sheet
If you wish to make use of the Google Sheet, the best approach I do know proper now
is:
- Open it up
- File » Make a replica…
- Save a model to your personal Google Drive
- Export your Request Map knowledge as a CSV
- Import your personal knowledge into your duplicated sheet
- Choose column A2
- File » Import…
- Add
- Navigate to your personal CSV
- Substitute knowledge at chosen cell
- Import knowledge
- Take away any duplicate or superfluous rows and knowledge
Closing
Within the occasions I’ve used these instruments and methods to debate third events with
shoppers, I’ve all the time discovered that issues have gone much more easily than
pointing fingers and taking a extra ruthless method. No one appreciates being
advised that their predominant contributions to the web site make it slower. Having uncooked
knowledge, coupled with an ask, don’t inform perspective, typically yields way more
beneficial outcomes. I’ve made nice headway by adopting this technique—I hope it
helps you, too.

