Over on my Dig Deep Health weight lifting software, I exploit magic hyperlinks for passwordless logins. One of these authentication workflow takes an electronic mail tackle and sends a one-time-use hyperlink that can routinely log the given person into my ColdFusion software, no password required. A couple of weeks in the past, I began seeing SPAM bots submit this type (for causes that I can not perceive). To fight this malicious assault, I added Google’s reCAPTCHA v3 to my login kind. This was the primary time that I’ve used reCAPTCHA in a ColdFusion software; so, I assumed it is perhaps price a better look.
“CAPTCHA” stands for “Utterly Automated Public Turing check to inform Computer systems and People Aside”. It represents a class of automated instruments that assist defend on-line websites from being abused by malicious actors. reCAPTCHA is Google’s implementation of such a device. And, “v3” is the newest implementation of reCAPTCHA on the time of this writing.
reCAPTCHA v3 makes use of a workflow that features each client-side and server-side facets. On the client-side, Google’s JavaScript library makes an attempt to guage the kind of shopper that’s loading the web page (ie, is it a human or a bot). This contains making a cross-domain API name again to the Google servers as a way to generate a “problem token”. This problem token is then submitted as a hidden kind subject together with the HTML kind (that’s being protected).
On the ColdFusion facet, when processing stated kind, we then need to confirm this problem token in opposition to the Google API. The response from the Google API tells us whether or not or not the problem token is legitimate (ie, does it match a token that the client-side script provisioned); and, it offers us a rating between 0.0 and 1.0 that tells us how possible the requesting shopper is to be a human or a bot.
On this weblog publish, I need to take a look at each the server-side and the client-side code, beginning with the mechanics of verifying the problem token on the ColdFusion server.
Making exterior API calls in ColdFusion is at all times an attention-grabbing endeavor as a result of it forces us to consider the separation of issues. At first blush, making an API name may appear easy – simply use the CFHttp tag; and, that is finally what we’ll do. However, by drawing boundaries round completely different issues throughout the API consumption, we are able to create code that’s simpler to grasp and simpler to take care of.
In the case of consuming an HTTP-based service, I wish to isolate the mechanics of the HTTP request / response life-cycle from the remainder of the code. This enables me to maintain the calling code extra semantic and fewer noisy. What I ended up creating is a two element system:
-
ReCaptchaGateway.cfc– the ColdFusion element that handles the low-level HTTP mechanics of the exterior API name. -
ReCaptchaClient.cfc– the ColdFusion element that wrangles the inputs, orchestrates the API name, and evaluates the API response.
The ReCaptchaGateway.cfc is a lightweight wrapper across the CFHttp tag. All it does is provoke the exterior HTTP request after which parse the response:
element
output = false
trace = "I present low-level API strategies for validating Google reCAPTCHA challenges."
{
/**
* I initialize the reCAPTCHA gateway with the given parameters. This gateway performs
* low-level HTTP requests to the distant Google API however doesn't interpret the response
* (apart from to parse and return the serialized response payload).
*/
public void operate init(
required string apiKey,
numeric timeoutInSeconds = 5
) {
variables.apiKey = arguments.apiKey;
variables.timeoutInSeconds = arguments.timeoutInSeconds;
}
// ---
// PUBLIC METHODS.
// ---
/**
* I confirm the given reCAPTCHA token supplied by the client-side problem.
*/
public struct operate verifyToken(
required string token,
required string ipAddress,
numeric timeoutInSeconds = variables.timeoutInSeconds
) {
cfhttp(
consequence = "native.apiResponse",
methodology = "publish",
url = "https://www.google.com/recaptcha/api/siteverify",
getAsBinary = "sure",
timeout = timeoutInSeconds
) {
cfhttpparam(
sort = "formfield",
title = "secret",
worth = apiKey
);
cfhttpparam(
sort = "formfield",
title = "response",
worth = token
);
cfhttpparam(
sort = "formfield",
title = "remoteip",
worth = ipAddress
);
}
var fileContent = getFileContentAsString( apiResponse );
if ( isFailureResponse( apiResponse ) ) {
throw(
sort = "ReCaptcha.Gateway.RequestError",
message = "Google reCaptcha token verification failure.",
element = "Returned with standing code: #apiResponse.statusCode#",
extendedInfo = fileContent
);
}
attempt {
return( deserializeJson( fileContent ) );
} catch ( any error ) {
throw(
sort = "ReCaptcha.Gateway.ParseError",
message = "Google reCaptcha response couldn't be parsed.",
element = "Returned with standing code: #apiResponse.statusCode#",
extendedInfo = fileContent
);
}
}
// ---
// PRIVATE METHODS.
// ---
/**
* I return the given fileContent payload as a UTF-8 encoded string. Although we're
* asking the CFHttp tag to return the fileContent as a Binary worth, the kind is simply
* assured if the request comes again correctly. If one thing goes terribly improper
* (similar to a "Connection Failure"), the fileContent will nonetheless be returned as a easy
* string. This methodology will normalize each response instances to a string.
*/
non-public string operate getFileContentAsString( required struct apiResponse ) {
if ( isBinary( apiResponse.fileContent ) ) {
return( charsetEncode( apiResponse.fileContent, "utf-8" ) );
}
return( apiResponse.fileContent );
}
/**
* I decide if the given API response has a failure (ie, non-2xx) standing code.
*/
non-public boolean operate isFailureResponse( required struct apiResponse ) {
return( ! apiResponse.statusCode.reFind( "2dd" ) );
}
}
Since this can be a self-contained demo, I’ve included non-public strategies – getFileContentAsString() and isFailureResponse() – for low-level manipulation. However, if this have been a extra strong software, I might possible issue these strategies out into some form of “HTTP Utilities” element the place they could possibly be shared throughout any variety of API wrappers.
I am without end fascinated with a Sandi Metz presentation through which she mentioned a college of thought whereby any non-public methodology must be made right into a public methodology on one other object. The concept being that any non-public strategies are more likely to signify a “conduct” that may be recognized and encapsulated in one other object with cleaner boundaries. Typically it appears loopy; and, typically, it appears sensible!
The objective of this ColdFusion element – and all of my “gateway” parts – is to encapsulate low-level interactions on the “edge” of the system; the place management leaves my software and is handed over to a different software (or service).
An occasion of this ColdFusion element can then be supplied to the ReCaptchaClient.cfc element as a “conduct”. Which means, it may be supplied as a dependency that implements some abstracted motion with out the calling context having to grasp the implementation particulars. This enables our ReCaptchaClient.cfc to deal with the “enterprise logic” of a reCAPTCHA workflow with out having to fret concerning the underlying HTTP mechanics.
This element exposes one major methodology – verifyToken() – which makes the API name to confirm the problem token; after which ensures that the API response comprises a rating that signifies a “human” actor (and never a bot). It additionally supplies a secondary methodology – testToken() – which merely throws an error if the verifyToken() name returns false. I discover a majority of these throw-based strategies very nice to make use of inside a multi-step workflow.
Within the following code, discover that an occasion of ReCaptchaGateway.cfc is being supplied as a constructor argument:
element
output = false
trace = "I present high-level strategies for validating reCAPTCHA challenges."
{
/**
* I initialize the reCAPTCHA shopper with the given parameters.
*/
public void operate init( required any reCaptchaGateway ) {
variables.gateway = arguments.reCaptchaGateway;
}
// ---
// PUBLIC METHODS.
// ---
/**
* I check the given reCAPTCHA token supplied by the client-side problem. If the
* problem passes efficiently, this methodology exits quietly. In any other case, this methodology
* throws an error.
*/
public void operate testToken(
required string token,
required numeric scoreThreshold,
required string ipAddress
) {
if ( ! verifyToken( argumentCollection = arguments ) ) {
throw(
sort = "ReCaptcha.Consumer.VerifyError",
message = "Google reCaptcha verification failure.",
element = "Problem was not profitable, person is perhaps a bot."
);
}
}
/**
* I confirm the given reCAPTCHA token supplied by the client-side problem. Returns
* true if the problem handed and false in any other case.
*/
public boolean operate verifyToken(
required string token,
required numeric scoreThreshold,
required string ipAddress
) {
// If no token has been supplied by reCAPTCHA's client-side interception, then we
// know that the person is trying to bypass our safety protocols. There is no
// must make the API name to confirm.
if ( ! token.len() ) {
return( false );
}
var apiResponse = gateway.verifyToken( token, ipAddress );
// The "success" flag merely signifies that the supplied problem token was legitimate
// and matches an unused token that Google has on its facet. This, alone, doesn't
// imply that the requesting shopper is a human.
if ( ! apiResponse.success ) {
return( false );
}
// The reCAPTCHA rating ranges from 0.0 to 1.0 (11 inclusive readings). This
// determines how possible the requesting shopper is to be a human. 0.0 means very
// more likely to be a BOT. 1.0 means very more likely to be a HUMAN.
return( apiResponse.rating >= scoreThreshold );
}
}
As you may see, after we name verifyToken() or testToken(), we should cross in a scoreThreshold. Google’s reCAPTCHA system would not inform us if a given shopper is a human or a bot — it tells us how possible it’s {that a} given shopper is a human or a bot. It’s then as much as us, as product engineers, to resolve how strict we have to be within the given HTML kind.
Sadly, the reCAPTCHA documentation on this matter is not tremendous prescriptive. It mainly says, when there is a decrease interplay rating, try to be extra restrictive in your software (and probably add additional authentication steps in your given workflow). It additionally says you would possibly need to observe the reCAPTCHA scores in manufacturing for some time earlier than really verifying them on the server-side:
As reCAPTCHA v3 would not ever interrupt the person stream, you may first run reCAPTCHA with out taking motion after which resolve on thresholds by your site visitors within the admin console. By default, you need to use a threshold of 0.5.
This final line – “By default, you need to use a threshold of 0.5” – is not even very clear. I assume what it means is that utilizing a threshold of 0.5 is an efficient place to begin when differentiating between bots and people. If that is the case, it would make sense to set 0.5 as a default for scoreThreshold. However, for the second, I might somewhat push that duty up the stack to the calling context (leaving it as a required parameter).
Now that we now have our reCAPTCHA ColdFusion parts able to go, we have to combine the reCAPTCHA client-side code into our login kind. This may be finished imperatively with JavaScript; or, it may be finished declaratively with data- attributes (and a callback). For the sake of simplicity, I am utilizing the declarative strategy.
The declarative strategy works by adorning the submit button with data- attributes and a CSS class that point out which buttons to look at and which operate to name as soon as the problem token has been provisioned. As soon as the problem token has been provisioned (and routinely injected into the HTML kind), we are able to use the callback to explicitly proceed with the shape processing.
Within the following ColdFusion code, I’ve put collectively a one-page workflow that comprises the shape processing logic on the prime and the shape HTML on the backside. For the sake of simplicity, I am instantiating the ReCaptchaClient.cfc on each web page request (as an alternative of caching it in a persistent scope):
<cfscript>
// SECURITY CAUTION: You shouldn't present the SECRET KEY to anybody. It is a set of
// throw-away keys that I've created particularly for this demo.
config = {
siteKey: "6LdiDTUpAAAAAJ62pHfEm8Cn6tD4a84XWxBuejDf",
secretKey: "6LdiDTUpAAAAAK7KDXfQ6aBCHpEATcZHikm-XUzi"
};
// Utilizing Inversion of Management (IoC) to create the gateway element after which present
// it to the reCAPTCHA shopper element as a dependency.
// --
// NOTE: Usually, I'd cache this ColdFusion element in a persistent scope; however,
// for the sake of the demo and ease, I'm re-creating it on each request.
reCaptchaClient = new ReCaptchaClient(
new ReCaptchaGateway( config.secretKey )
);
// ------------------------------------------------------------------------------- //
// ------------------------------------------------------------------------------- //
param title="kind.submitted" sort="boolean" default=false;
param title="kind.username" sort="string" default="";
param title="kind.password" sort="string" default="";
// This subject is routinely populated by the client-site reCAPTCHA problem.
// Google's script will intercept the shape submission course of, consider the shopper
// requesting the submission, populate this type subject, after which proceed with the
// regular kind submission (by way of the supplied callback).
param title="kind[ 'g-recaptcha-response' ]" sort="string" default="";
errorMessage = "";
if ( kind.submitted ) {
attempt {
// NOTE: Every reCAPTCHA token is simply legitimate for 2-minutes and may solely be
// verified as soon as as a way to forestall replay assaults.
reCaptchaClient.testToken(
token = kind[ "g-recaptcha-response" ],
scoreThreshold = 0.5,
ipAddress = cgi.remote_addr
);
// TODO: Precise authentication logic for the applying ...
location(
url = "./house.cfm",
addToken = false
);
} catch ( ReCaptcha.Consumer.VerifyError error ) {
errorMessage = "Your login kind has expired. Please attempt submitting your kind once more.";
} catch ( any error ) {
errorMessage = "An surprising error occurred."
}
} // END: Submitted.
</cfscript>
<cfoutput>
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8" />
<meta title="viewport" content material="width=device-width, initial-scale=1" />
</head>
<physique>
<h1>
Google reCAPTCHA V3 Demo In ColdFusion
</h1>
<cfif errorMessage.len()>
<p>
<sturdy>Error:</sturdy> #encodeForHtml( errorMessage )#
</p>
</cfif>
<kind id="login-form" methodology="publish">
<enter sort="hidden" title="submitted" worth="true" />
<p>
<sturdy>Username:</sturdy><br />
<enter sort="textual content" title="username" dimension="30" />
</p>
<p>
<sturdy>Password:</sturdy><br />
<enter sort="password" title="password" dimension="30" />
</p>
<p>
<!--
These "data-" attributes inform reCAPTCHA that it must intercept the
kind submission and inject a problem token. The information-callback
operate will probably be invoked with the problem token as soon as it's obtained.
-->
<button
sort="submit"
data-sitekey="#encodeForHtmlAttribute( config.siteKey )#"
data-action="submit"
data-callback="handleToken"
class="g-recaptcha">
I am completely a Human, Login!
</button>
</p>
</kind>
<!---
Load reCAPTCHA script and supply submission callback.
// --
FROM THE DOCUMENTATION: Usually talking, the extra context that reCAPTCHA
has a couple of web page, the higher knowledgeable it's to find out whether or not person actions
are authentic. That is notably true when utilizing variations of reCAPTCHA
that do not depend on person challenges. Thus, ready to load reCAPTCHA till a
particular restricted motion happens (for instance, kind submission) is mostly
not really useful.
--->
<script src="https://www.google.com/recaptcha/api.js"></script>
<script sort="textual content/javascript">
// As soon as Google generates a problem token and injects it into the shape as a
// hidden enter ("g-recaptcha-response"), it can invoke this callback. We
// should then proceed on with the submit workflow.
operate handleToken( token ) {
doc.getElementById( "login-form" )
.requestSubmit()
;
}
</script>
</physique>
</html>
</cfoutput>
As you may see, we do not actually do a lot on this CFML. The shape submission is routinely intercepted and the problem token is routinely injected into the HTML kind. The one factor that we now have to do is confirm the problem token on the prime of the shape processing as a way to be certain that the requesting person is an actual human.
Now, after we render our ColdFusion login kind, there are two issues to note. First, we see a reCAPTCHA badge show-up (unobtrusively) on the bottom-right fringe of the web page:
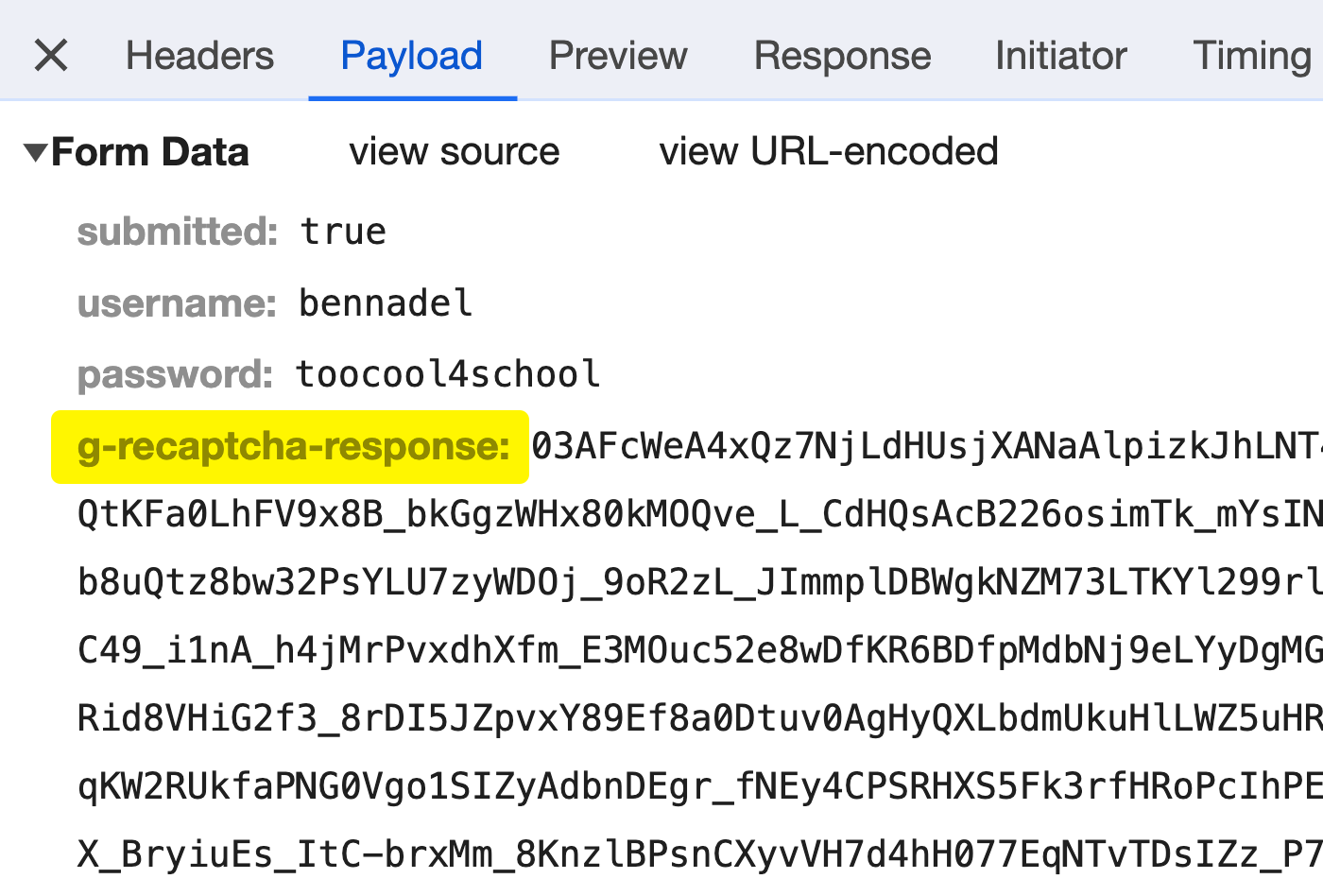
And, after we submit the shape, we are able to see the reCAPTCHA problem token routinely exhibiting up within the HTML kind knowledge:
As soon as this request lands on the ColdFusion server, we then cross it into the testToken() methodology; which, behind the scenes, is making an API name again to Google with the problem token. With some added logging, I can see that the API response is that this:
{
"success": true,
"rating": 0.9,
"motion": "submit",
"hostname": "localhost",
"challenge_ts": "2023-12-19T12:13:05Z"
}
As you may see, Google reCAPTCHA is simply 0.9 assured that I am a human. However, hey, that is ok for this login kind since we’re utilizing 0.5 because the rating threshold.
Ultimately, I am excited to say that by including reCAPTCHA v3 to my ColdFusion health software, I’ve utterly eradicated the earlier bot-based SPAM assaults! I nonetheless see the malicious site visitors coming via; however, not one of the requests make it previous the problem token verification step.
Wish to use code from this publish?
Try the license.


